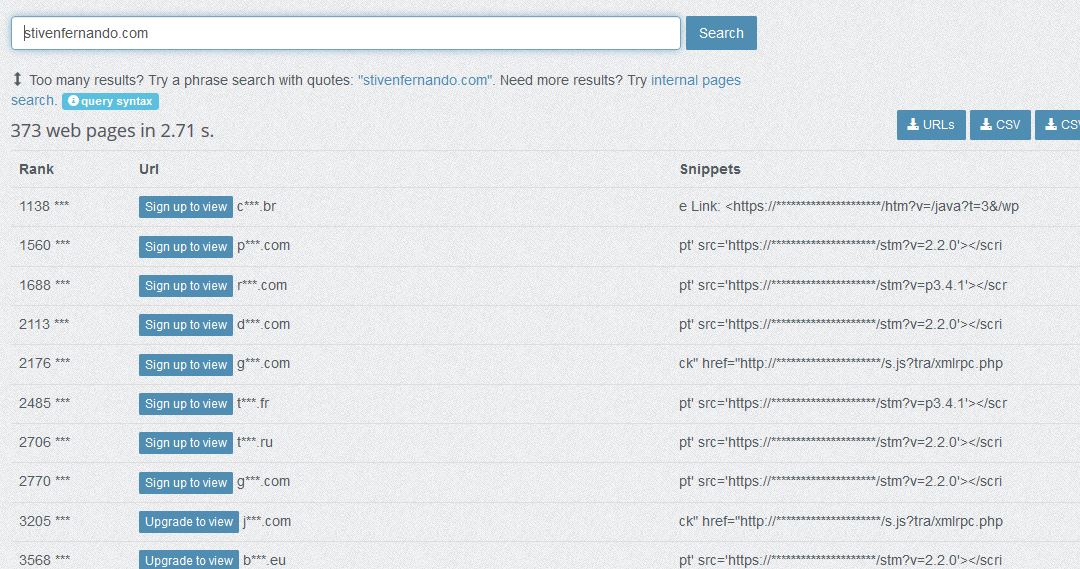
Recently I came across this recent contamination, which affects more sites each day.
According to publicwww, there are aprox. 300 affected URLs:
Javascript malware is hosted on US based server 162.241.149.182, and will redirect users to various landing pages, hosted on Digitalocean servers: 134.209.192.77, 157.245.79.75.
A good antivirus like ESET or Bitdefender, should prevent website visitors from getting browser adware.
Need help? Let us clean your site.
Malicious links reported:
https://ws.stivenfernando.com/fanta.js?
https://ps.stivenfernando.com/r2.php
https://ws.stivenfernando.com/htm?v=
https://ws.stivenfernando.com/stm?v=
https://ws.stivenfernando.com/s.js?tra
A backup is required beforehand, to prevent any data loss.
After dashboard access is restored, a database tool should be used to restore siteurl and home entries from wp_options table.
Easiest way would be to edit wp-config.php file via FTP or hosting dashboard ( replace example.com with your own domain name ).
define( 'WP_HOME', 'http://example.com' ); define( 'WP_SITEURL', 'http://example.com' );
Look for “String.fromCharCode”, “stivenfernando” and “list.insertBefore(s, list.childNodes[0])”.
Insert the following script with pack.php file and place it inside your root folder. This way you can pack all PHP and JS files, which can be cleaned locally.
<?php
exec("find . -name '*.php' -o -name '*.js' | tar -cvzf php-js.tar.gz -T -");
phpinfo();
?>
Search and replace tools for malicious strings inside multiple files: dnGrep, grepwin, VisualGrep ( mac ), powergrep ( paid ).
Attackers usually alter wp_posts and wp_options tables.
This will prevent having infected cached pages listed on Google.
Secondary malicious URLs:
https://ps.stivenfernando.com/r2.php
https://0.dexterfortune.com
https://1.dexterfortune.com
https://2.dexterfortune.com
https://0.donaldbackinsky.com
https://1.donaldbackinsky.com
https://2.donaldbackinsky.com
https://temp.adsforbusines.com
https://b.bestdealfor1.life
https://bladecentos4.live
https://a.bestdealfor1.life
https://bestprize-places-here.life
https://adaranth.com/afu.php?zoneid=2579905
Other domains: checkandgo.info, traffsend.me, check-you-robot.online, allowandgo.com, bo4news.biz, nclubs.xyz, terrout7.biz, koolernews.biz
Try our Free site check.