Today one customer reported a recurrent database contamination.
Site URL was injected with: https://check.resolutiondestin.com/wt.js
Also posts table injected with: hxxps://check.resolutiondestin.com/t.js
Need help? Let us clean your site.
Malicious URLs and domains, hosted on 162.241.175.185:
https://check.resolutiondestin.com/bolj
https://tds.resolutiondestin.com
resolutiondestin.com
result.resolutiondestin.com
check.resolutiondestin.com
hxxps://check.resolutiondestin.com/m1.js
hxxps://check.resolutiondestin.com/jsc.js
https://check.resolutiondestin.com/wss.js
hxxps://2.jockersunface.com
jockersunface.com
https://9.jockersunface.com
bo4news.biz
jockersunface.com
netspooke1.biz
terrout7.biz
weenews.biz
lodder4.biz
loderik.club
anwapfile.work
lifecontext.me
lodder.club
loderik.info
mirox22.biz
newspu03.site
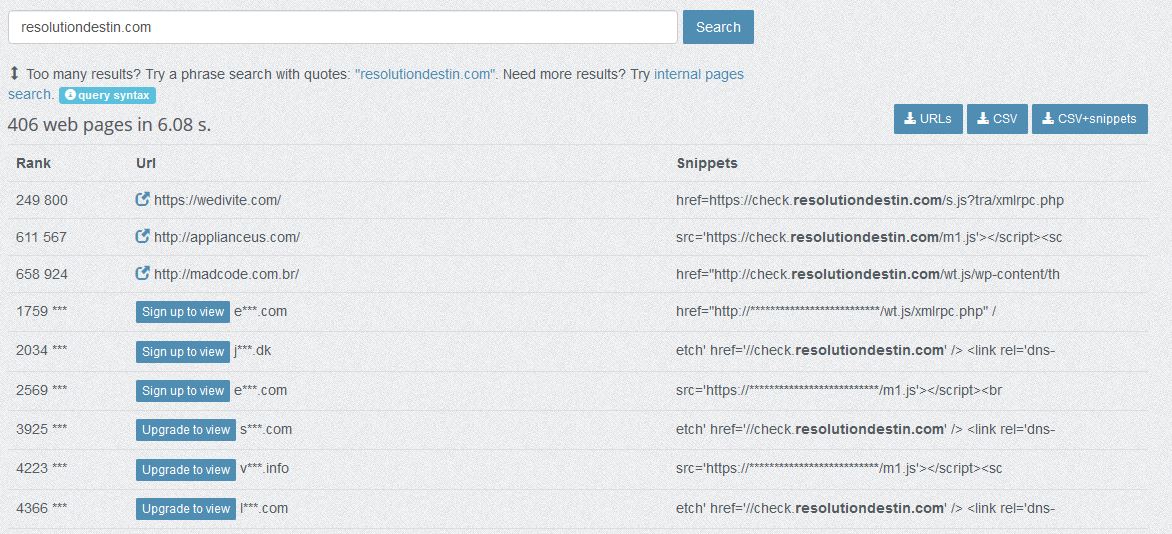
So far there are aprox. 400 reported cases, according to publicwww:
If you’re facing the same issue, in order to sort this issue, you should follow these steps:
1. Perform backup and change database password.
2. Regain dashboard admin access.
To reset site URL, check this article: https://wordpress.org/support/article/changing-the-site-url/
If you can edit wp-config.php file, add this code ( replace example.com with your own domain name ).
define( 'WP_HOME', 'http://example.com' ); define( 'WP_SITEURL', 'http://example.com' );
3. Clear SQL injections
a) Run this SQL query ( make sure you backup first ):
UPDATE wp_posts SET post_content = REGEXP_REPLACE(post_content, '<script(.*?)>((.|\n)*?)<\/script>', '');
or
b) Use Better search replace: https://wordpress.org/plugins/better-search-replace/
Search for:
<script type=text/javascript src='hxxps://check.resolutiondestin[.]com/t.js'>
And replace with nothing ( leave the field empty ).
Try our Free site check.