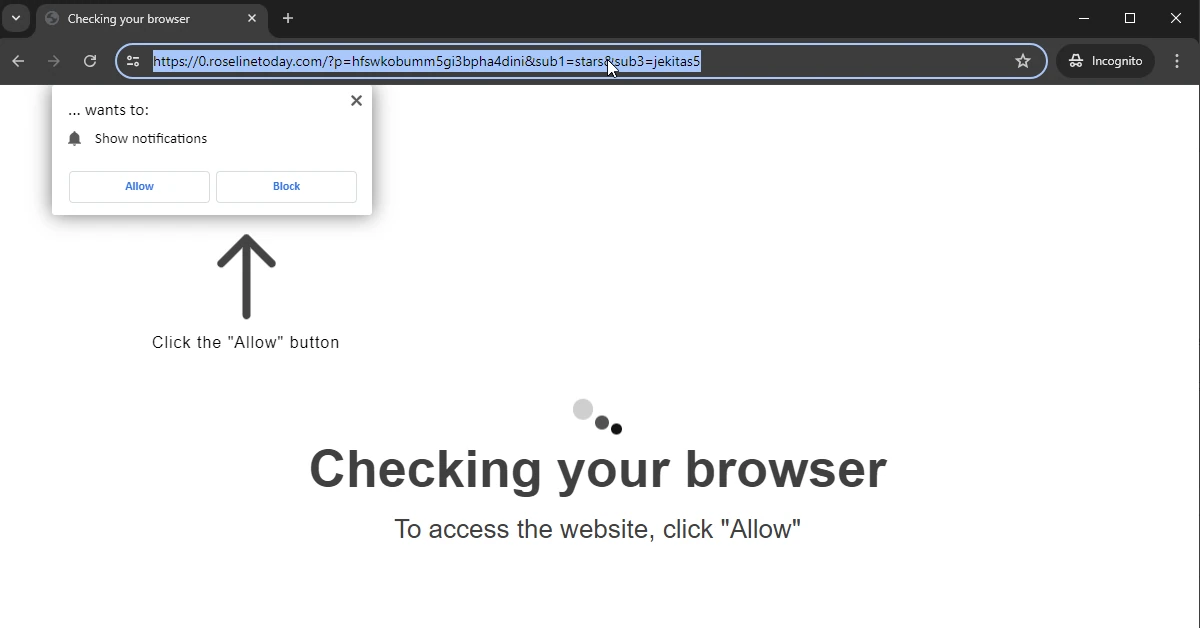
Recently, we noticed several websites with suspicious redirects to 0.bluelitetoday.com. After a careful review, we found multiple files contaminated, including injected index.php and functions.php files, and unauthorized users with admin privileges.
Note: If the code snippets plugin is activated but not showing in the WordPress dashboard, malicious code in the ‘wp_options’ table may be the cause.
Think your website is infected?
Try our Free site check.
Cleanup steps
- Site backup, including local files and database.
- Disable public access, to prevent further data loss.
- Site cleanup – make sure each site component is safe.
- Blacklist check.
FAQs
What’s the first thing we always do, before proceeding with a cleanup?
Each time we proceed by securing the local files, including the contaminated scripts, to a safe area outside of public access – it will prevent data loss and reputation damage. After this step, a temporary HTML index file is created, which contains critical contact information – phone number, address, and links to social media.
What tool will clear the malware?
We don’t use automated tools to clean a website. Malicious scripts are built to pass malware scans so it’s better to perform a manual cleanup and check each component by hand. After the cleanup is complete, we usually install and configure a firewall.
Malware returned after the cleanup. What to do?
That’s a sign of cross-site contamination – quickly isolate the website by moving the files to a safe area and finding other neighbor websites hosted on the same server.
Also, check the raw access logs, and look for any suspicious PHP files, custom CronJobs, suspicious plugins, users, etc.
Malicious code:
<style id="tdw-css-placeholder">.stephuofgycnpvhnlzbf{} .step4636435346{}</style><script>var a=1;var b=2;var c=4;</script>;style></style>
Malicious links:
2th level links
https://cdn.rdntocdns.com/rthrttu.php
https://away.taskscompletedlists.com/jtytyusy
https://come.taskscompletedlists.com/7MjvR5
https://go.recordsbluemountain.com/7MjvR5
https://gogo.recordsbluemountain.com/zbLzKF
https://to.taskscompletedlists.com/Qvr4Tm
https://rain.recordsbluemountain.com/8YkzBStf
https://four.startperfectsolutions.com/scripts/sold.js
3th level links
https://0.bluelitetoday.com/?p=hfswkobumm5gi3bpha4dini&sub1=cars&sub3=jekitas5
https://0.bluefiretobind.com/index.php?p=gmzdkzdfmq5dcobygyza&sub1=clerss&sub3=fkitas2
https://0.squereredpoints.com/?p=hbsgcnzqhe5gi3bpha4dsoa&sub1=squrrelboy&sub2=redsun
https://0.bluelitetoday.com/?p=hbsgcnzqhe5gi3bpha4dsoa&sub1=squrrelgirl&sub2=redsun
Malicious ASNs: AS199058 ( SERVA ONE LTD )
Malicious IPs: 89.42.142.89, 188.72.219.35
Cloudflare nameservers:
1. taskscompletedlists.com
Cloudflare nameservers: otto.ns.cloudflare.com, aitana.ns.cloudflare.com ( reported on 7/27/2024 )
SERVA ONE LTD [email protected]
2. 0.bluelitetoday.com:
Cloudflare nameservers: gemma.ns.cloudflare.com, anderson.ns.cloudflare.com ( reported on 7/26/2024 )
DigitalOcean LLC, [email protected]
3. startperfectsolutions.com
Cloudflare nameservers: ximena.ns.cloudflare.com, mitchell.ns.cloudflare.com
Hosting provider: Zomro B.V., [email protected]
4. recordsbluemountain.com
Cloudflare nameservers: gemma.ns.cloudflare.com, anderson.ns.cloudflare.com ( reported on 7/29/2024 )
Hosting: Zomro B.V., [email protected]
5. rdntocdns.com
Cloudflare nameservers: venus.ns.cloudflare.com, margo.ns.cloudflare.com ( reported on 8/1/2024 )
6. squereredpoints.com
Cloudflare nameservers: fatima.ns.cloudflare.com, chris.ns.cloudflare.com ( reported on 9/25/2024 )
First seen: June 30, 2024
If you’ve recently noticed suspicious redirects to 0.bluelitetoday.com and 0.roselinetoday.com, we can help.
Our skilled malware analysts are available 24/7 to fix hacked WordPress websites and clean up malware – reach out to us if you need help.
Hacked website?
Try our Free site check.
A security analyst will perform a free thorough external site check within the next minutes.