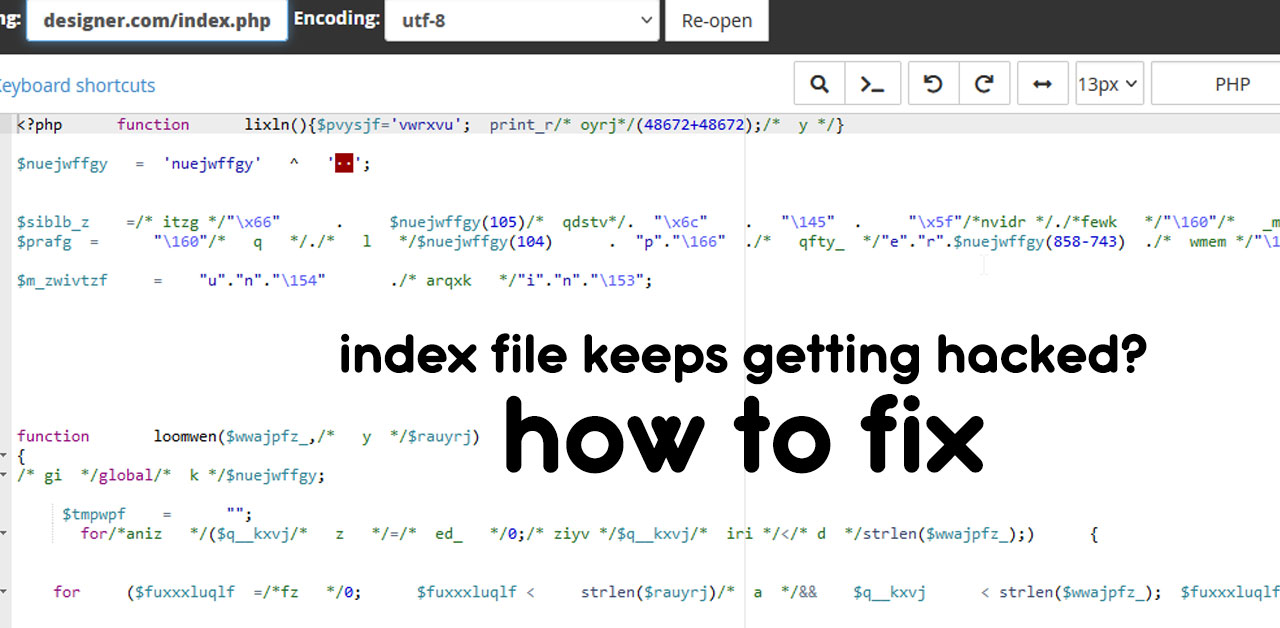
PHP files can be infected with malware through various means, often due to vulnerabilities in the website.
Here are some common ways the index.php PHP file can become re-infected:
Try our Free site check.
1. A background malicious shell script, which is executed once and stays on.
2. Through an infected core, plugin or theme file or a backdoor PHP file.
3. A Cron Job installed by the attacker.
4. Manually, via sFTP, FTP or any file manager available.
To quickly address the issue you may:
1. Restore a clean index.php file and apply write protection, by setting permission to 444. Also, the public_html or the parent folder can be set to 555.
2. Perform a site backup to secure the current data, in case anything goes wrong.
3. Run a malware scan and clean all the malicious files.
4. Apply all the available updates, starting with the security updates.
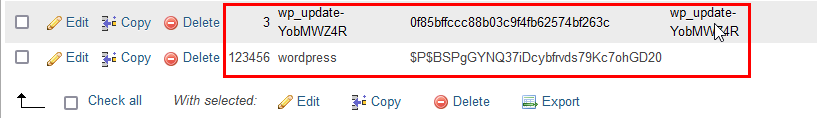
5. Review the users with the administrator role.
To prevent any PHP file from getting infected:
Regular Updates: Keep your PHP version, CMS (like WordPress, Joomla, etc.), plugins, and themes updated to the latest versions to patch known vulnerabilities.
Security Measures: Implement security measures like firewalls, intrusion detection systems, and security plugins to prevent attacks.
Input Validation: Validate and sanitize user inputs to prevent SQL injection, XSS, and other attacks.
File Permissions: Set appropriate file permissions to prevent unauthorized modifications.
If you suspect the index PHP file has been infected, it’s crucial to isolate all the affected files, remove the malicious code, and restore clean versions from backups if available. Additionally, a security expert can assist in thoroughly cleaning and securing your website.
MAGEFIX SecurityMalware cleanup & protectionTry our Free site check.