Today, we cleaned another website with various signs of contamination, including injected index.php files, malicious users with admin privileges, and malicious plugins installed.
Since the contamination was widespread, I decided to review each site component. After the cleanup was complete, I disabled all the users with admin privileges, and also I switched off the plugin installation feature.
Do you think your website is infected?
Try our Free site check.
FAQs
How to disable plugin installation in WordPress:
Just add the following line inside the wp-config.php file
define('DISALLOW_FILE_MODS', true);
What’s the first thing we always do, before proceeding with a cleanup?
We always start by moving all the contaminated web files to a safe area outside of public access – it will prevent data loss and reputation damage. After we secure the files, a temporary HTML index file is created, which contains critical contact information – phone number, address, and links to social media.
Which security plugin fixes the problem?
We never use a plugin to clean a website – that’s because malicious programs are always built to pass malware scans. It’s better to perform a manual cleanup and check each component by hand. After the cleanup is complete, we usually install and configure Wordfence.
I cleaned the website myself, and the malware returned. What to do?
That’s usually a sign of cross-site contamination – quickly disable the website by moving the files to a safe area and finding other neighbor websites hosted on the same server.
Also, check for any suspicious PHP files, custom Cronjobs, suspicious plugins, users, etc.
Cleanup steps
- Make sure the WordPress files are intact and updated – including index.php and wp-config.php files.
- Review the themes and plugins folders, apply all the available updates – delete the malicious folders.
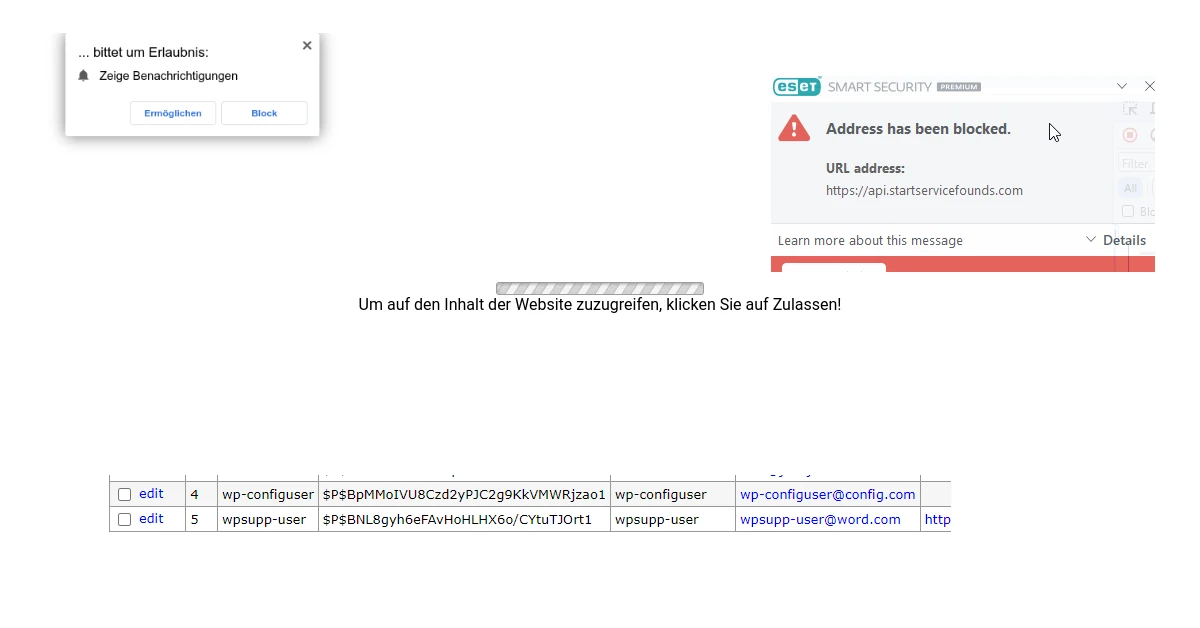
- Review users with admin privileges – look for wp-configuser and wpsupp-user.
Malicious plugins:
wp-cleansong/wp-cleansong.php
wp-restoresp
Malicious URLs
First redirects
https://ready.linetoslice.com/scripts/spectr.js?v=325
https://ready.perfectlinestarter.com/2hZQjb
https://sources.readytocheckline.com/VVsxS1
https://from.startfinishthis.com/j77jns
https://render.linetowaystrue.com/2DTKZF
https://start.linetowaystrue.com/QWnHWM
https://finish.linetowaystrue.com/XfhWyW
Second redirects
https://0.restwaytofindreds.com/?p=hbsgcnzqhe5gi3bpha4dsoa&sub2=renaaat2&sub3=sp2
https://0.bluelitetoday.com/?p=hfswkobumm5gi3bpha4dini&sub1=scars&sub3=jekitas2
https://0.roselinetoday.com/?p=hfswkobumm5gi3bpha4dini&sub1=stars&sub3=jekitas5
Malicious IPs: 45.9.148.92
Cloudflare nameservers:
1. linetowaystrue.com
dolly.ns.cloudflare.com, trevor.ns.cloudflare.com
2. perfectlinestarter.com
otto.ns.cloudflare.com, aitana.ns.cloudflare.com
3. bluelitetoday.com
anderson.ns.cloudflare.com, gemma.ns.cloudflare.com
4. roselinetoday.com
anderson.ns.cloudflare.com, gemma.ns.cloudflare.com
5. linetoslice.com
johnny.ns.cloudflare.com, irma.ns.cloudflare.com
6. rdntocdns.com
margo.ns.cloudflare.com, venus.ns.cloudflare.com
https://0.inputgreensorts.com/?p=mnstgnldme5gi3bpha3tqnq&sub1=simn
https://bluefiretoline.com/?p=gjswkm3bha5gi3bpha3teoi&sub2=freli
https://0.bluefiretoline.com/?p=gjswkm3bha5gi3bpha3teoi&sub2=freli
https://0.brownsisteroftime.com/index.php?p=mi3dcoddgq5dcnzvgu3a&sub2=lkfert
https://0.greensisteroftime.com/index.php?p=mi3dcoddgq5dcnzvgu3a
adi.ns.cloudflare.com, maxim.ns.cloudflare.com
Other malicious URLs
https://bind.bestresulttostart.com/scripts/statistics.js?s=11.4.2
193.163.7.113, AS204601
https://chest.cdntoswitchspirit.com/scripts/connections.js
camilo.ns.cloudflare.com, gina.ns.cloudflare.com
https://0.redfiretoline.com/?p=gjswkm3bha5gi3bpha3teoi&sub2=rosa
martin.ns.cloudflare.com, rosalyn.ns.cloudflare.com
https://js.cdntoswitchspirit.com/source/split.js
camilo.ns.cloudflare.com, gina.ns.cloudflare.com
https://rest1.rdntocdns.com/DGC4PH
https://jquery.restartyourchoices.com/cdncollect
ganz.ns.cloudflare.com, gina.ns.cloudflare.com
https://cdn.rdntocdns.com/rthrttu.php
45.9.149.210, AS49447
https://rest1.rdntocdns.com/DGC4PH
45.9.149.210, AS49447
https://dns.startservicefounds.com/service/f.php
45.150.67.235, AS44477
https://api.startservicefounds.com/service/f.php
45.150.67.235, AS44477
Other malicious domains: 0.redfiretoline.com, 0.brownsisteroftime.com, redfiretoline.com, 0.cleanblueitems.com, 0.inputgreensorts.com, inputblacksorts.com, cleanreditems.com, 0.greensisteroftime.com.
Sucuri SiteCheck:
Known javascript malware: malware.injection?35.70
If you’ve recently noticed suspicious redirects to from.startfinishthis.com, 0.inputgreensorts.com, or 0.bluefiretoline.com subdomains, we can help.
Our skilled malware analysts are available 24/7 to fix hacked WordPress websites and clean up malware – reach out to us if you need help.
Hacked website?
Try our Free site check.
A security analyst will perform a free thorough external site check within the next minutes.