If you’re researching on how to clean piterreceiver.ga malware, you may consider our free site check.
Need help? Let us clean your site.
Related guides > How to remove trick.trainresistor.cc malware.
If your Google Ads are currently suspended we recommend our Platinum plan, which will include malware cleanup and Ads support:
https://www.magefix.com/platinum/
This contamination may affect both database and web files, so I would recommend to:
a) Check other sites hosted on the same hosting account.
If malware infection is widespread, each site should be isolated, to prevent cross-site contamination.
b) Perform a site cleanup for each WordPress instance, checking plugins, theme and core files.
To fix a hacked website, follow these steps:
2. Disable MySQL remote access, especially if you’re using Plesk.
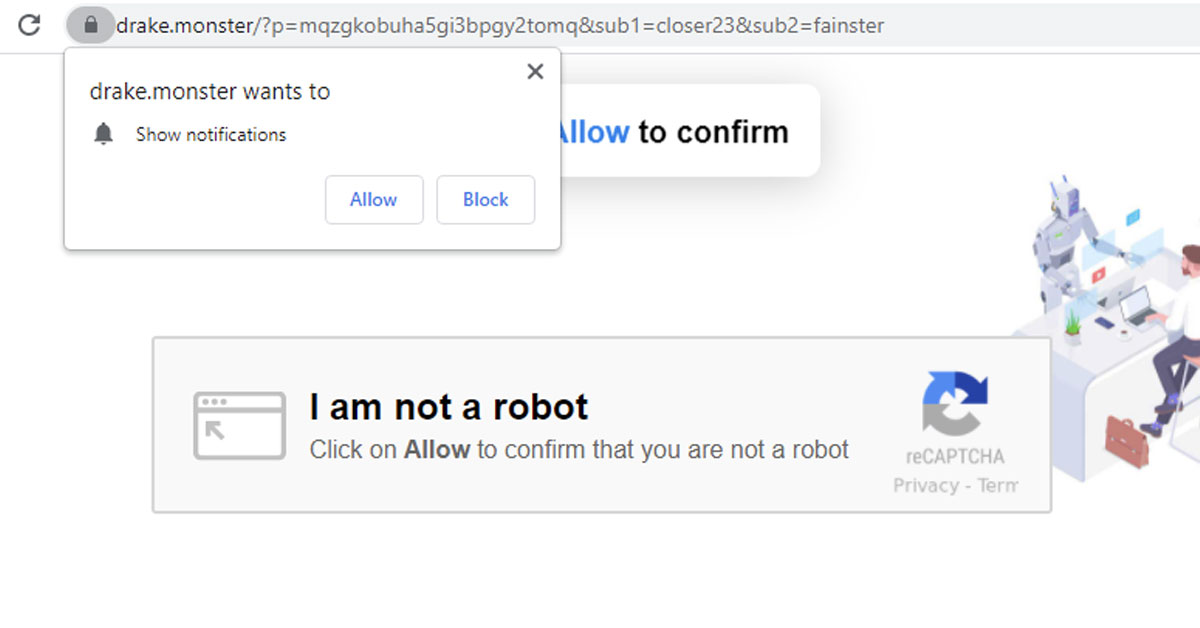
Look for “String.fromCharCode”, “piterreceiver”, and “store.piterreceiver.ga”.
Insert the following script inside pack.php file and place it inside your root folder. This way you can pack all PHP and JS files, which can be cleaned locally.
Search and replace tools for malicious strings inside multiple files: dnGrep, grepWin, VisualGrep, PowerGREP.
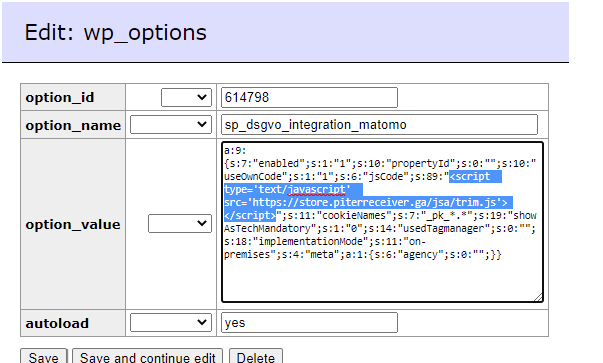
- As a precaution measure, look for “piterreceiver”, “String.fromCharCode”. This way you will know if other tables are infected as well.
Injections usually target wp_posts and wp_options tables.
The following SQL commands may be used to clear any malicious JS:
- Check users with administrator privileges.
Search and replace database tool for malicious strings: Better Search Replace, Search Replace DB ver. 4.
This way, any infected cached pages listed on Google will be updated.
Make sure other sites hosted on the server are secured and isolated.
More info: https://wordpress.org/support/plugin/shapepress-dsgvo/
Safe plugin version: https://downloads.wordpress.org/plugin/shapepress-dsgvo.3.1.23.zip
Make sure the following table entry is cleaned ‘sp_dsgvo_integration_matomo’.
Try our Free site check.
Malicious URLs:
https://store.piterreceiver.ga/jsa/trim.js
https://steam.piterreceiver.ga/pm.php
https://storage.piterreceiver.ga
https://store.piterreceiver.ga/track/go.php
https://store.piterreceiver.ga/gateway.php
https://white.belonnanotservice.ga/jpGvcN
https://dreamjunior.best/w_40.js
https://carlsponsors.best
https://serch26.biz/sw/w1s.js
https://store.piterreceiver.ga/Ld5WGw
https://small.piterreceiver.ga/team.php?id=685486-44-334u87-234
https://blink.piterreceiver.ga/slow.php
https://left.trainresistor.cc/clear.js
Malicious domains: trainresistor.cc, piterreceiver.ga, belonnanotservice.ga, dorbluess.bar, cleverysystems.best, drake.monster, demetravertando.best, dorbluess.best, anwapfile.bar, anwapfile.monster, checkrobotics.club, checkrobotics.com, cleverysystems.bar, cleverysystems.best, demetravertando.bar, demetravertando.best, zigmundred.bar, zigmundred.best, keltonchain.bar, fastfuturelist.top, clearyfastexam.best.
Malicious code
Malicious IPs:
80.78.24.100, 188.166.68.96, 134.209.199.15, 185.230.143.101, 45.9.150.63, 109.234.33.9, 45.9.150.64 ( Nice IT Services )
illustration by @Dom J.