These days we noticed higher than usual contamination with this script. If your website is blacklisted for malicious content, and this URL is being reported: cdn.examhome.net, then it means your database is contaminated.
Before anything else, you should backup your database & site files to prevent any data loss.
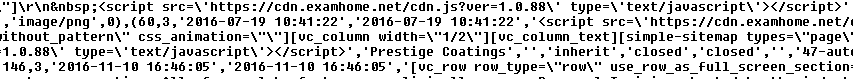
Secondly, in order to remove this malicious injection, all you have to do is to search & replace the following string with no content.
<script src=\'hxxps://cdn.examhome[.]net/cdn.js?ver=1.0.88\' type=\'text/javascript\'></script>
These are several tools for this procedure:
1. Search Replace DB: https://interconnectit.com/products/search-and-replace-for-wordpress-databases/
2. Better Search Replace: https://wordpress.org/plugins/better-search-replace/
If you decide to use interconnectit script, don’t forget to delete it after you’ll complete the search & replace.
If the above Javascript code is not found, then try this code:
<script src='hxxps://cdn.examhome[.]net/cdn.js?ver=1.0.88' type='text/javascript'></script>
Lastly, you should check your local files. Look out for this string:
<script language=javascript>var _0xfcc4=[
If you’re dealing with a general contamination, it will be a good idea to rebuild your WordPress website, using fresh core files, plugins & theme, since we don’t recommend the search & replace technique for local files. In case you’re looking for help, contact us.
Useful links:
Sucuri labs, Multi-Vector WordPress Infection from Examhome: http://labs.sucuri.net/?note=2018-09-18
Sucuri scanner: https://sitecheck.sucuri.net/
Cleanup plans: https://www.magefix.com/pricing