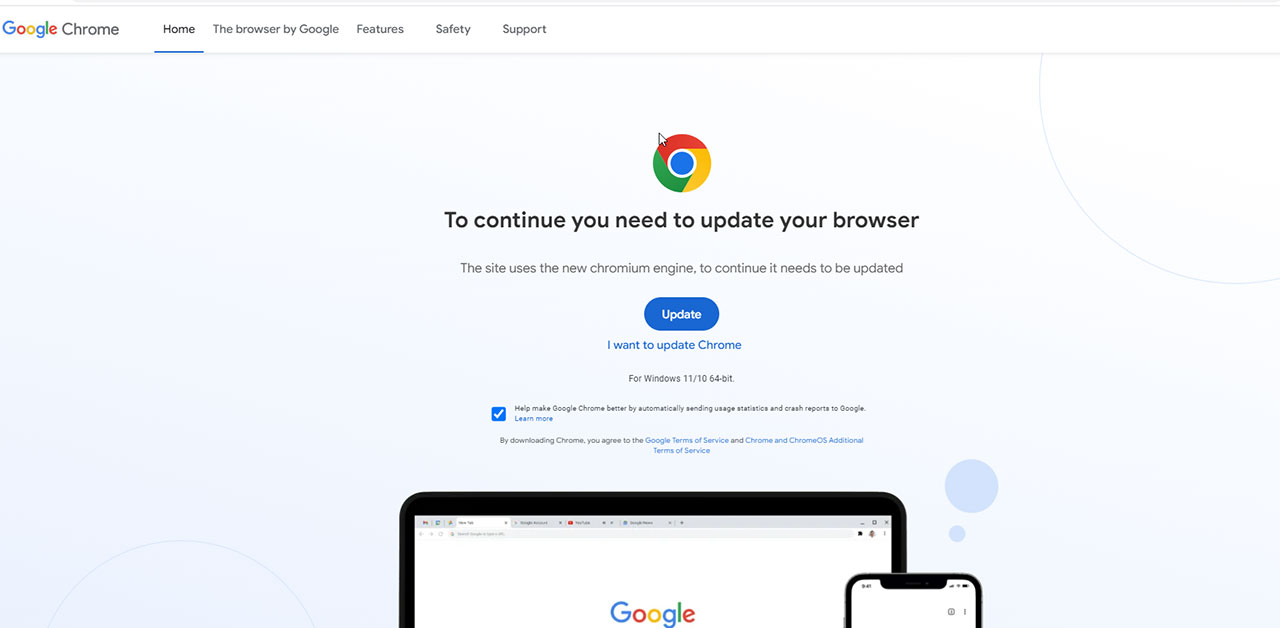
According to PublicWWW, there are approximate 925 websites confirmed to have the Chrome update hack.
Try our Free site check.
What have the sites infected by this malware have in common?
After investigating the last websites affected by the Chrome update defacement, all have in common the WordPress platform.
How does this malware works?
All the index.php and index.html files are overwritten with a 291 KB HTML file, copied from this URL https://www.google.com/intl/en_uk/chrome/. A regular WordPress index file has 405 bytes or less, which is 0.4 KB. The HTML file contains a download link to a *.zip file.
Quick temporary solution
Restore all the index files and set the permission to 444 – read only. How to find all the index files? – run this script.
How to recover from the Chrome update hack?
- Backup the infected site(s), including database and web files.
- For each WordPress site, restore core files, plugins and themes, one by one, manually, making sure you’ll not use any files from the backup – start fresh.
- If any of the neighbor static sites is compromised, try to recover the index files from the Google cache or by using Wayback Machine Downloader.
- Check the admin users list and and disable any suspicious accounts.
- Backup and review the wp_options table.
- Ask for a reindex via Google search console. If the domain is blacklisted, ask for a security review.
- Apply all the security updates available and use PHP version 7.4 or greater.
- Scan all the sites for cross-site contamination – if other folders are affected, isolate the static sites from the WordPress ones.
If you seek professional help to cover all the above steps, check our Platinum plan.
https://members.magefix.com/product/platinum/
Malicious URLs & IPs
185.126.219.203, https://usesoft.net/temp/EngineChromium.zip
185.48.181.88, https://efesmarble.com/temp/spp/rf/Installer.zip
108.179.192.227, https://tcastro.com/temp/ChromiumEngine.zip
82.98.155.244, https://ingenieriainsitu.com/temp/WebViewEngine.zip
212.1.208.232, https://elevenexpress.com.co/temp/BrowserModule.zip
185.126.219.204, https://my.hoqer.com/temp/WebModuleBrowser.zip
https://placengine.site/index.php ( base64 encoded )
https://chromiumengine.space/get.html
Malicious code
“/assets/autotrack.js”
“saved from url=(0041)https://www.google.com/intl/en_uk/chrome/”
Misleading text
To continue you need to update your browser
The site uses the new chromium engine, to continue it needs to be updated
Sucuri SiteCheck ( Defacement Found )
Known javascript malware: defacement?fake_update.001.02
Domain blacklisted by Google Safe Browsing? – you may notice a warning screen.
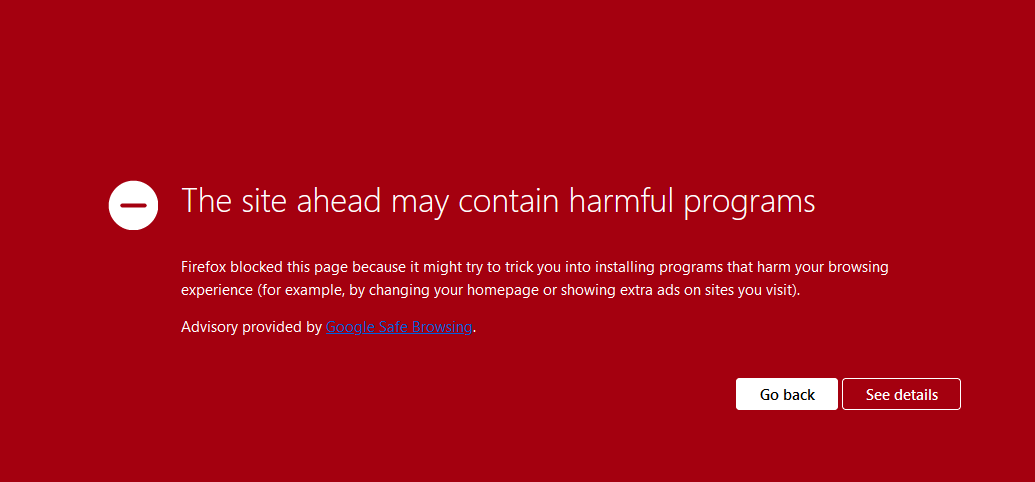
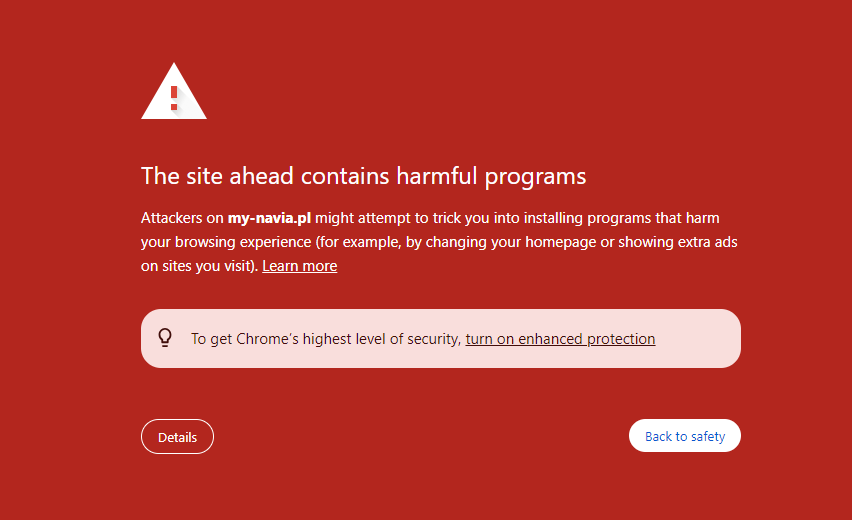
Try our Free site check.
Malicious files inside the .zip file
WebViewEngine.exe 8.51 MB (8,930,458 bytes)
BrowserModule_Setup.exe 8.55 MB (8,968,524 bytes)
File description: Shop affordable hearing aids online. Made in the USA. High-quality digital hearing aids sold to consumers and delivered to your door.
unpack200.exe, pack200.exe.
Documented on Sucuri blog