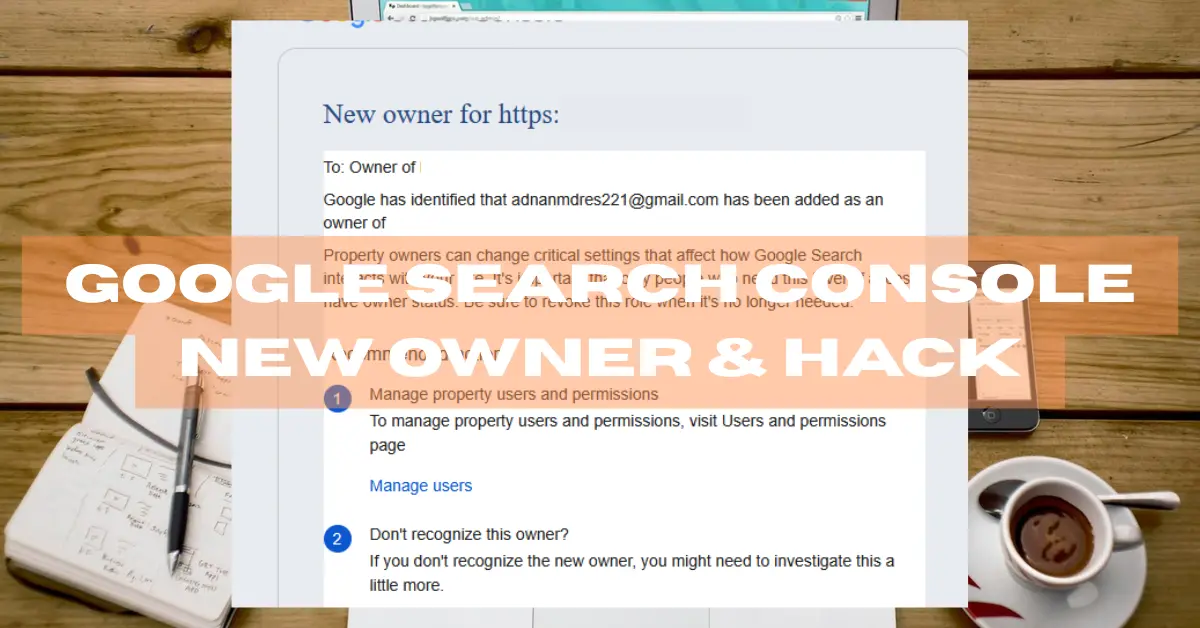
Recently, a customer signaled that a new Google search user was registered using the file upload method. Since the email address was not authorized, a website hack was suspected.
After checking the recently uploaded files, we found out “Porto2025güncel.zip” was uploaded, containing malicious PHP files, a bad robots file, and a sitemap.xml file.
Try our free site check.
A malware analyst will provide a security report for your website.
We immediately performed a backup, followed by a malware cleanup, ensuring all the site components were updated & secure—the website runs WordPress.
Here are the steps we took:
- Site backup and visible malware removal from the root folder;
- Google Search Console check, remove the unauthorized users, check the submitted sitemap files;
- We run a complete WordPress cleanup process, making sure plugins, themes, and core files are secure and updated;
- Configured the firewall & monitored for any suspicious activity; and
- Lastly, we reviewed the logs file and blocked suspicious IPs that may’ve been used during the attack.
If you get a similar notification from the Google search console, immediate action is required to counter the contamination and prevent SEO spam, data loss, and reputation damage.
Google search notification: Google has identified that [email protected] has been added as an owner.
Malicious files: Porto2025güncel.zip
amp.php, google934cf6c2262c7adf.html