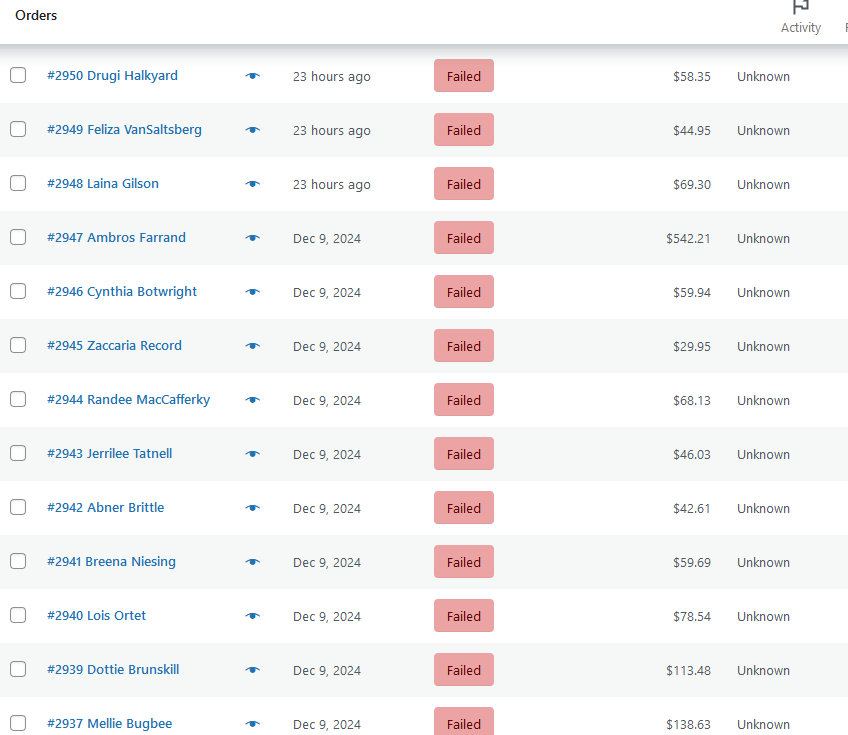
We recently noticed several websites being bombarded with many failed new orders, resulting in downtime and slowdowns. Since the attack is carried out from various networks and countries, it’s very difficult to counter the malicious activity.
Try our free site check.
Stop fake orders
- Review the traffic logs and get more information about the abusive IPs. IPinfo example: https://ipinfo.io/136.227.183.193
- Block the IP range or the entire ASN.
- A more strict approach would be to block all countries, allowing US and the country where your shop is serving.
- Enable and configure the reCAPTCHA for WooCommerce plugin – not recommended for long-term use as it may affect conversion rate.
Block spam order with similar patterns, using functions.php code:
#1 block /wp-json/wc/store/checkout requests, thanks to denialdesign.co.uk
/** disable wc_endpoint to stop carding attacks **/
function disable_wc_endpoint() {
$current_url = $_SERVER['REQUEST_URI'];
if (strpos($current_url, '/wp-json/wc/store/checkout') !== false) {
wp_redirect(home_url('/404.php'));
exit;
}
}
add_action('rest_api_init', 'disable_wc_endpoint');
#2 block /wp-json/wc/store/v1/checkout requests
/** disable wc_endpoint to stop carding attacks **/
function disable_wc_endpoint_v1() {
$current_url = $_SERVER['REQUEST_URI'];
if (strpos($current_url, '/wp-json/wc/store/v1/checkout') !== false) {
wp_redirect(home_url('/404.php'));
exit;
}
}
add_action('rest_api_init', 'disable_wc_endpoint_v1');
#3 We targeted orders with same billing company name and billing city ( not efficient )
add_action( 'woocommerce_checkout_process', 'afm_validation' );
function afm_validation() {
// get the company and city
if(isset($_POST['billing_company'])) $billing_company_mf = $_POST['billing_company'];
if(isset($_POST['billing_city'])) $billing_city_mf = $_POST['billing_city'];
if( $billing_company_mf == $billing_city_mf ) {
wc_add_notice( __("Suspicious order, please contact support."), "error" );
}
}
Delete spam orders
- Run WP CLI to bulk delete orders, order status: wc-completed, wc-pending, wc-cancelled, wc-failed
wp post delete $(wp post list --post_type='shop_order' --post_status=wc-failed --format=ids) --force
Malicious POST requests:
136.227.160.207 - - [01/Dec/2024:09:38:56 -0500] "GET /wp-json/wc/store/products?stock_status=instock&order=asc&orderby=price&min_price=1&max_price=5000&type=simple&page=1&per_page=100 HTTP/1.1" 200 136.227.160.207 - - [01/Dec/2024:09:38:57 -0500] "GET /wp-json/wc/store/cart HTTP/1.1" 200 2290 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML like Gecko) Version/17.3.1 Safari/605.1.15" 136.227.160.207 - - [01/Dec/2024:09:38:59 -0500] "POST /wp-json/wc/store/cart/add-item HTTP/1.1" 201 6967 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML like Gecko) Version/17.3.1 Safari/605.1.15" 136.227.160.207 - - [01/Dec/2024:09:39:00 -0500] "POST /wp-json/wc/store/cart/update-customer HTTP/1.1" 200 7212 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML like Gecko) Version/17.3.1 Safari/605.1.15" 136.227.160.207 - - [01/Dec/2024:09:39:01 -0500] "POST /wp-json/wc/store/cart/select-shipping-rate HTTP/1.1" 200 7212 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML like Gecko) Version/17.3.1 Safari/605.1.15" 136.227.160.207 - - [01/Dec/2024:09:39:04 -0500] "GET /checkout/ HTTP/1.1" 200 169404 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML like Gecko) Version/17.3.1 Safari/605.1.15" 136.227.160.207 - - [01/Dec/2024:09:39:07 -0500] "POST /?wc-ajax=ppc-data-client-id HTTP/1.1" 200 1282 "https://domain.com/checkout/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML like Gecko) Version/17.3.1 Safari/605.1.15" 136.227.160.207 - - [01/Dec/2024:09:39:10 -0500] "POST /?wc-ajax=ppc-create-order HTTP/1.1" 200 862 "https://domain.com/checkout/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML like Gecko) Version/17.3.1 Safari/605.1.15" 136.227.160.207 - - [01/Dec/2024:09:39:12 -0500] "POST /?wc-ajax=ppc-approve-order HTTP/1.1" 200 768 "https://domain.com/checkout/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML like Gecko) Version/17.3.1 Safari/605.1.15" 136.227.160.207 - - [01/Dec/2024:09:39:13 -0500] "POST /wp-json/wc/store/checkout HTTP/1.1" 400 2627 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML like Gecko) Version/17.3.1 Safari/605.1.15"
Bad networks & IPs:
AS20473 – The Constant Company, LLC
136.227.177.0/24
134.199.78.0/24
136.227.160.0/24
136.227.183.0/24
AS6939 – Hurricane Electric LLC
96.62.244.0/23
150.241.242.0/23
150.241.250.0/23
AS49544 – i3D.net B.V
162.245.204.0/22
31.204.128.0/19
AS9009 – M247 Europe SRL
38.132.118.0/24
37.120.213.0/24
146.70.28.0/24
152.89.162.0/24
192.145.127.0/24
AS22773 – Cox Communications Inc.
98.167.0.0/17
Resources:
https://www.denialdesign.co.uk/blocking-card-testing-attacks-in-woocommerce/
https://wordpress.org/support/topic/spam-fraud-orders
If you’ve recently noticed a high number of failed orders, we can help.
Our skilled malware analysts are available 24/7 to secure WordPress websites and clean up malware – reach out to us if you need help.
Hacked website? Try our free site check.
A security analyst will perform a free thorough external site check within the next minutes.