Lately, we have noticed many injection attempts from 172.245.168.36 (HostPapa), 118.169.93.198 (Taiwan). Wordfence blocks these attacks with the following message: “Blocked for XSS: Cross Site Scripting in POST body”.
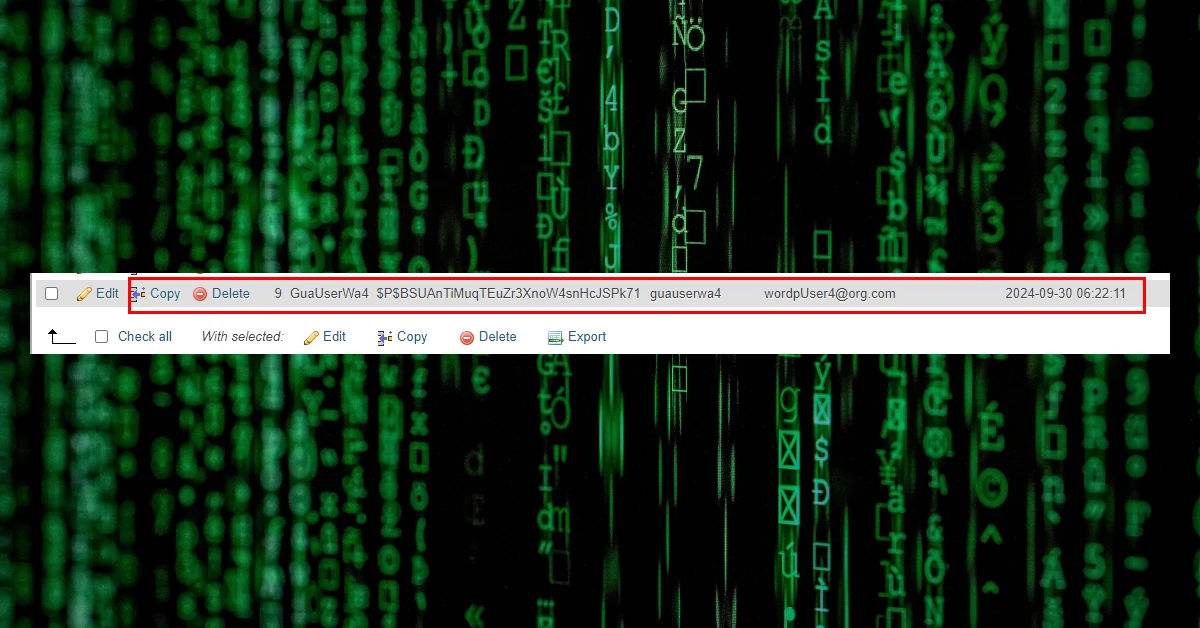
If a new user with admin privilege is created, that means your website is compromised, and you should address the situation as soon as possible.
Think your website is infected?
Try our Free site check.
Cleanup steps
- Clear “zeroday2024.com” or “tapspowdercoating.instawp.xyz” scripts using a search and replace tool.
- Switch all the users with administrator rights except the one you’re using and change your password afterward.
- Perform malware cleanup, making sure all the site components including plugins, themes, and core files are malware-free.
- Check to see if your domain is blacklisted by any security vendor.
- If your website was affected by malicious redirects, verify your URL with GSC and ask for a re-index.
- Monitor the website, check for any suspicious activity, and install a firewall.
Malicious URLs:
https://tapspowdercoating.instawp.xyz/wp-includes/js/jquery_v2.2.js
https://zeroday2024.com/admin-bar-reloaded.min.js
https://wplicense.org/admin-bar-reloaded.min.js
Malicious IPs:
161.35.237.170, 118.169.93.198 ( Taiwan ).
More on this attack:
https://guides.magefix.com/2024/09/blocked-for-xss/
Malicios code:
https://gist.github.com/magefix/fdf7359b5dd530158081d2b866a143b1
Malicious logs:
172.245.168.36 (United States)
Blocked for XSS: Cross Site Scripting in POST body: result = ”
New User Registration:
GuaUserWa4 [email protected]
a:4:{s:3:"log";s:10:"GuaUserWa4";s:3:"pwd";s:15:"[email protected]@";s:9:"wp-submit";s:6:"submit";s:10:"testcookie";s:1:"1";}
GuaUserWa5, [email protected]
wpapitest, [email protected]
If you’ve recently noticed new administrator users created – we can help.
Our skilled malware analysts are available 24/7 to fix hacked WordPress websites and clean up malware – reach out to us if you need help.
Hacked website?
Try our Free site check.
A security analyst will perform a free thorough external site check within the next minutes.